Cisco SDWAN : Layer 3 TLOC Extension
Cisco SDWAN : Layer 3 TLOC Extension
A feature called TLOC extension enables a WAN Edge router to communicate with the neighboring WAN Edge router via a TLOC-extension interface through the WAN transport. Without requiring to be directly attached to both service provider clouds, the TLOC-extension capability enables the WAN transports to be extended to both SD-WAN routers.
The capability offers transparent connectivity from one interface (referred to as a TLOC extension interface) to a certain WAN transport and is configured per-interface.
There are two ways we can configure the TLOC extension in Cisco SDWAN fabric
- L2 when you connect another SDWAN router on the same site
- L3 when you connect through the non SDWAN router, needs L3 capabilities and GRE tunnel to extend the TLOC
⭐Related : HSECK9 License for Cisco C8000v SDWAN Router
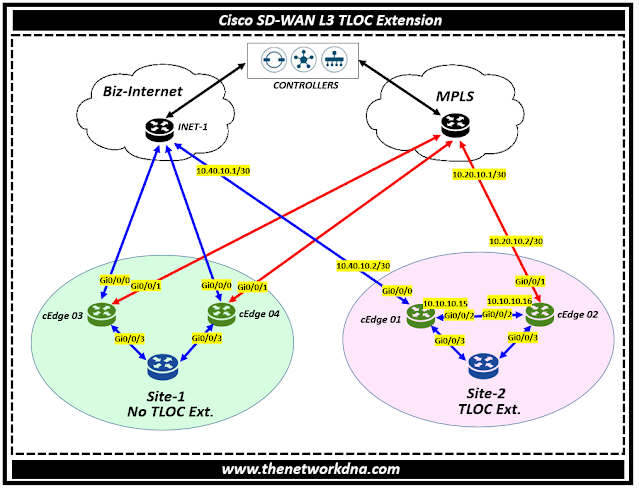
Let's take an scenario where we have a site-2 with two cEdges (cEdge 01 and cEdge 02) connected to the MPLS and biz-internet circuits respectively. What does that means ?
Well if you see, cEdge 01 is only connected to the internet and cEdge 02 is only connected to MPLS.
So now we are going to use the tloc-extension between cEdge 01 and cEdge 02 in order to extend the tunnel for MPLS and internet (biz-internet). As we see on cEdge 02 we have only mpls tunnel on the interface Gi0/0/1 as shown below
Extending "biz-internet" to cEdge 02 router which only has MPLS
cEdge 02 Router
Interface Gi0/0/1 is connected to MPLS service provider with the IP address and color MPLS restrict.
Note : We are using the CLI mode configuration, we will come up with another article where we will use feature templates.
Note : We are using the CLI mode configuration, we will come up with another article where we will use feature templates.
!
interface GigabitEthernet0/0/1
description MPLS
ip address 10.20.10.2 255.255.255.252
no ip redirects
ip tcp adjust-mss 1360
load-interval 30
negotiation auto
arp timeout 1200
service-policy output shape_GigabitEthernet0/0/1
end
!
interface GigabitEthernet0/0/1
tunnel-interface
encapsulation ipsec
no border
color mpls restrict
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
!
Now Let's configure Gi0/0/2 for the "tloc-extension" to extend the internet on cEdge 02 through cEdge 01 to the internet. We are using the color "biz-internet" for internet.
Step 1: Identify the color and the interface you are extending to and connect physical link between them on the interface Gi0/0/2 on both sides.
Step 2: Now you should have reachability between cEdge01 and cEdge 02. For that you need to add the configurations on the interface Gi0/0/2 on both sides.
Let's start with cEdge 01
NDNA-cEdge01# Config-transaction
NDNA-cEdge01(config)# vpn 0
NDNA-cEdge01(config-vpn-0)# interface GigabitEthernet0/0/2
NDNA-cEdge01(config-interface-gi0/0/2)# ip address 10.10.10.15 255.255.255.0
NDNA-cEdge01(config-interface-gi0/0/2)# no shut
NDNA-cEdge01(config-interface-gi0/0/2)# exit
NDNA-cEdge01(config-vpn-0)#commit
NDNA-cEdge01#
Now with cEdge 02
NDNA-cEdge02# Config-transaction
NDNA-cEdge02(config)# vpn 0
NDNA-cEdge02(config-vpn-0)# interface GigabitEthernet0/0/2
NDNA-cEdge02(config-interface-gi0/0/2)# ip address 10.10.10.16 255.255.255.0
NDNA-cEdge02(config-interface-gi0/0/2)# no shut
NDNA-cEdge02(config-interface-gi0/0/2)# exit
NDNA-cEdge02(config-vpn-0)#commit
NDNA-cEdge01#
Step 3: Extend the biz-internet from cEdge 02 to cEdge 01, If you see below the interface Gi0/0/2 which is connected to the cEdge 02 will be now using "tloc-extension" towards the internet service provider interface Gi0/0/0
NDNA-cEdge01# Config-transaction
NDNA-cEdge01(config)# vpn 0
NDNA-cEdge01(config-vpn-0)# interface GigabitEthernet0/0/2
NDNA-cEdge01(config-interface-gi0/0/2)# tloc-extension GigabitEthernet0/0/0
NDNA-cEdge01(config-interface-gi0/0/2)# exit
NDNA-cEdge01(config-vpn-0)#commit
NDNA-cEdge01#
Its not end, we need to create an tunnel interface on the cEdge 02 in order to make a BFD tunnel starting from cEdge 02 directly extended to internet over the cEdge and biz internet circuit from cEdge 01. We also need to add the static route on cEdge 02 pointed to the cEdge interface Gi0/0/2
NDNA-cEdge02# Config-transaction
NDNA-cEdge02(config)# vpn 0
NDNA-cEdge02(config-vpn-0)# interface GigabitEthernet0/0/2
NDNA-cEdge02(config-interface-gi0/0/2)# tunnel-interface
NDNA-cEdge02(config-tunnel-interface)# allow service all
NDNA-cEdge02(config-tunnel-interface)# color biz-internet
NDNA-cEdge02(config-tunnel-interface)# encapsulation ipsec
NDNA-cEdge02(config-tunnel-interface)# exit
NDNA-cEdge02(config-vpn-0)# ip route 0.0.0.0/0 10.10.10.15
NDNA-cEdge02(config-vpn-0)#commit
NDNA-cEdge02#
So still you will have the issue, Why ? your internet service provider don't know where this 10.10.10.16 exist which we put that on the interface Gi0/0/2 on cEdge 02 router. How to overcome that ?
In the case of directly connected interface or static routing, you need to tell your service provider to put a static route on their router pointing towards your cEdge 01 router as below. We are assuming that internet service provider router name is "INET"
INET # conf t
INET(config)# ip route 10.10.10.16 255.255.255.255 10.40.10.2
INET(config)# ip route 10.10.10.16 255.255.255.255 10.40.10.2
With the above static route on the Internet service provider router (INET) pointing towards your cEdge 01 router interface Gi0/0/0 will help to send back the traffic over the cEdge 01 and eventually to cEdge 02.
In scenario-2, we are going to extend the "MPLS" to cEdge 01 router which only has biz-internet.
Continue Reading...
- Finding the Right SD-WAN Vendor for Your Business
- The Evolution: Exploring the Origins of SD-WAN discussions
- Discover the Power of Multitenancy with Versa SDWAN!
- Introduction to Silver-Peak SDWAN Solution
- Introduction to VeloCloud SD-WAN Solution
- Introduction to Palo Alto's Prisma (CloudGenix) SDWAN
- Introduction to Fortinet SDWAN
Cisco SDWAN