Cisco Secure Firewalls: QOS policy and packet policing
Cisco Secure Firewalls: QOS policy and packet policing
As you may know that the Quality of Service (QoS) is a feature that rate limits network traffic that is allowed or trusted by access control. In Cisco Secure firewalls, QoS is supported only on the routed interfaces of threat defense devices, and is not supported on site-to-site VPN or VTI interfaces.
You can configure QoS on the security appliance to provide rate limiting on selected network traffic, for both individual flows and VPN tunnel flows, in order to ensure that all traffic gets limited bandwidth as per the administrator rules.
⭐Related : Cisco Secure Firewall Modes
⭐Related : Cisco Secure Firewall 7.x
⭐Related : Cisco Secure Firewalls models and Specifications
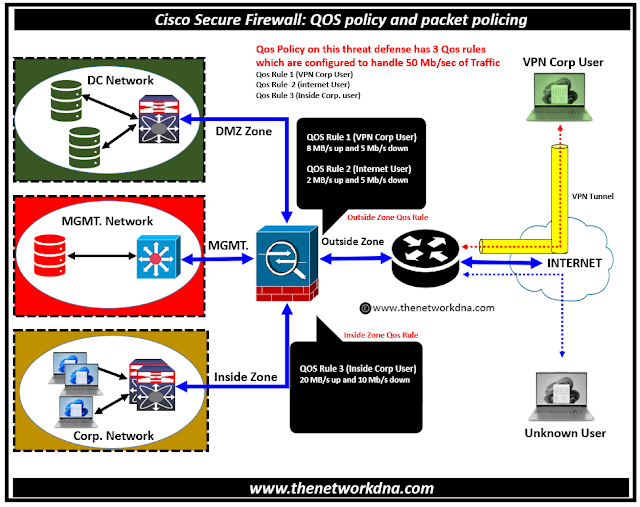
Fig 1.1- QOS policy and packet policing
Policing reduces traffic over a set limit. Policing is a method of ensuring that no traffic surpasses the maximum rate (in bits/second) that you have configured, ensuring that no single traffic flow or class can take up the entire resource. When traffic exceeds the maximum rate, the Cisco Secure firewall drops the excess traffic. Policing also establishes the maximum single burst of traffic allowed.
Cisco Secure Firewall can limit traffic rates to manage a network's bandwidth and assure quality of service (QoS) for business-critical applications. Lets see what we can do it on Cisco Secure firewall related to the Qos policies and rules
- Limit the rate of network traffic that has been approved or trusted by an access control rule.
- A threat defense uses a traffic policing system to control the flow of traffic.
- Drops excessive traffic when it hits a predetermined threshold.
- Multiple QoS rules exist within a single QoS policy.
- You can specify distinct upload and download speed restrictions for traffic that meets the requirements of a QoS rule.
- QoS rules based on IP address, port, application, URL, and user identification.
- Each QoS policy can have up to 32 QoS rules.
- Each interface that participates in a QoS policy must be in routed mode and associated with an interface object.
- It does not support traffic shaping, which involves queueing extra traffic in a buffer rather than dropping it for subsequent delivery.
- QoS policies cannot be applied to interfaces that are inline, passive, or switched.
Continue Reading...
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Cisco ASA Series 2: Configuring NAT
- Cisco ASA Series 3: Easy VPN Remote
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
- Cisco ASA Series 5: Configuring Threat Detection
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls