Cisco ASA Series 5: Configuring Threat Detection
Cisco ASA Series 5: Configuring Threat Detection
Cisco ASA is a security appliance that incorporates a firewall, antivirus software, intrusion detection, and a virtual private network (VPN). It allows for proactive threat defense, preventing attacks from propagating over the network.
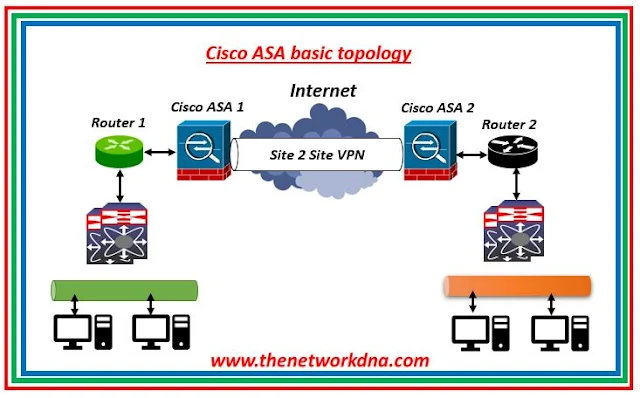 |
| Fig 1.1- Cisco ASA Basic Site 2 Site Topology |
To enable the security appliance to keep an eye on potentially dangerous packet flows, threat detection was included. In addition to alerting managers to potential attacks, this function is intelligent enough to automatically ban IP addresses or ranges that pose a concern (mostly through threat monitoring).
A technique for recognizing, comprehending, and thwarting threats before they affect the internal network architecture is called threat detection. It is dependent on several firewall triggers and data that are generated and computed when traffic flows through the ASA.
You can enable the threat detection functionality on any ASA running software version 8.0(2) or above, since it is supported starting with that version. Advanced Threat Detection TCP intercept data are only available in ASA 8.0(4) and above. Threat detection can be used to provide an extra layer of security to the fundamental security features of an ASA in situations when an IPS is unavailable, but it should not be confused with a dedicated IDS/IPS solution.
The threat detection function consists of three major components:
- Basic Threat Detection (by default activated)
- Advanced Threat Detection (by default, only ACL statistics are enabled)
- Threat Detection via Scanning (you can block hosts that scan the protected network).
⭐ Cisco ASA's Basic Threat Detection 🔐
By tracking the rates at which packets are discarded by the ASA as a whole for a variety of reasons, basic threat detection offers very rudimentary protection. Due to the lack of granularity to allow for very detailed monitoring, it offers basic capabilities as the name implies and is applied to the entire device.
⭐Imp : The ASA promptly sends a system log message (733100) upon detecting a threat.
Basic threat detection calculates the average rate interval (ARI), which varies from 600 seconds to 30 days, by measuring the rates at which drops occur for each event throughout the specified time period. The ASA views events as dangerous if the quantity of events occurring inside the ARI above the specified rate criteria.
To create the statistics, it often leverages the firewall's ASP-Drop engine.
- Packets that Access Lists (ACL Drop) reject.
- Invalid packet format (e.g., invalid-tcp-hdr-length or invalid-ip-header).
- Exceeded connection limitations (including configuration- and system-wide resource constraints).
- Attack of DoS detected (e.g., Stateful Firewall check failure, incorrect SPI).
- Basic firewall inspections were unsuccessful. (This option is a cumulative rate for all packet drops in this bulleted list that are due to firewalls). Drops unrelated to firewalls, such as interface overload, packets rejected during application inspection, and identified scanning attacks, are not included.)
- Noticed suspicious ICMP packets.
- Applications were not properly inspected, and there was an overflow of interfaces.
- Attack detection using scanning The initial TCP packet is not a SYN packet, or the TCP connection failed the three-way handshake—these types of scanning attacks are monitored by this option. This scanning attack rate data is used by full scanning threat detection, which uses it to categorize hosts as attackers and automatically ban them, among other things.)
- SYN Attack Recognition. Sessions with incomplete detection, such those with no data and/or TCP SYN attacks, are identified.
⭐ CLI Command configuration 📜
⭐ Web GUI configuration 💻
Configuration →Firewall →Threat Detection in the ASDM.
Continue Reading...
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls







