Overview of Cisco ASA/PIX Multiple Context Virtualization
Overview of Cisco ASA/PIX Multiple Context Virtualization
The ASA/PIX multiple context capability divides a single ASA or PIX device into numerous virtual devices, each with its own security policy, interfaces, and administrators. This capability is beneficial for service providers, large organizations, or campuses who want to differentiate between various consumers, departments, or networks.
However, several functionalities, such as VPN, multicast, and dynamic routing protocols, are not available in multiple context mode. A license is also required to activate multiple context mode on your device.
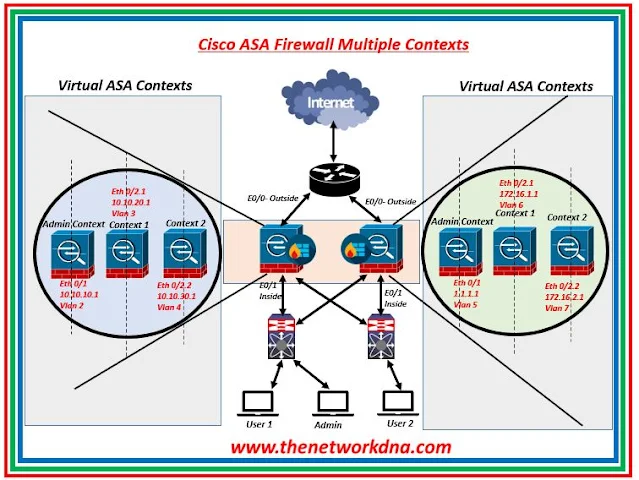 |
| Fig 1.1- Cisco ASA/PIX Multiple Context Virtualization |
🎪 Where to use Multiple Context ?
- When ISPs provide security services to a large number of clients, they employ a cost-effective, space-saving approach.
- Large corporations that keep their sections fully separate.
- Multiple context anytime a network necessitates the use of more than one security appliance.
🎪 What are types of Multiple Context ?
- System Context : The system administrator installs and controls contexts in the system configuration by configuring each context configuration location, allotted interfaces, and other context operational characteristics. The system configuration defines the security appliance's fundamental parameters. Except for the administrative interface, you cannot assign any IP addresses while in the system context. Only in the System EXEC mode, not in the other context modes, can you upgrade or downgrade the Cisco ASA software.
- Admin Context : The admin context is similar to any other context, except that when a user signs in to it, that person gains system administrator rights and may access the system as well as all other contexts. The admin context settings must be stored on Flash memory. When you go from Single to Multiple Context mode, the admin context is established automatically, and the configuration file is saved to the flash memory. This context might be coupled with any other ordinary user context or devoted to itself.
- Normal Context : This context is utilized where we partitioned the firewall. Console, Telnet, SSH, and ASDM can all be used to access contexts. When you log in to a non-admin context, you can only view that context's configuration.
⭐Note : The ports on the switch that are connected to ASA must be in trunk mode since multiple VLAN traffic has to travel through it once the ASA interfaces are broken into sub−interfaces.
You can’t rename the context, you will have to delete it, then create a new one with the new name. As we say, multiple context mode in the firewall supports only static routing.
🎪 Configuration Setup
When you convert from single mode to multiple mode, the security appliance converts the running configuration into two files:
- New startup configuration that comprises the system configuration.
- admin.cfg that comprises the admin context (in the root directory of the internal Flash memory).
- The original running configuration is saved as old_running.cfg (in the root directory of the internal Flash memory).
- The original startup configuration is not saved.
- The security appliance automatically adds an entry for the admin context to the system configuration with the name "admin."
🎪 Configuring Contexts on ASA
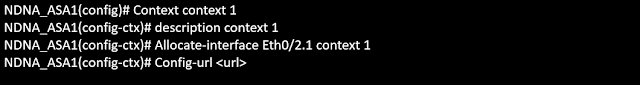
Here check out the configuration to create a ASA context as shown below in the snapshot ( Just an example)
You can’t rename the context, you will have to delete it, then create a new one with the new name. As we say, multiple context mode in the firewall supports only static routing.
You need to configure a static route for every non-directly connected subnet for a firewall context or set up a static default route. All adjacent routers should be also configured with static routes to allow for full connectivity.
🎪 Firewall Context Routing
Because firewall contexts do not share IP routing tables, you will require one of the following to establish connections between routing contexts:
- Configure each context with a set of static routes for the subnets connected or located behind the other context.
- Use an external router that has full knowledge of the subnets behind each of the contexts to provide connectivity.
Contexts Classification : It is easy to assign an input packet to the context if the interface where it has been received is uniquely allocated to the context. If the interface is shared, additional rules are needed.
🎪 Shared interfaces classification
- The firewall looks at the destination MAC address of the packet and the destination MAC designated the “next-hop” for the packet.*
- If the MAC address is the same in both contexts for the same interface, the firewall attempts to resolve the "conflicts" using NAT settings in each context. This can occur if you purposefully provide the same IP address to both contexts or do not allocate distinct MAC addresses to the common interfaces.
- In each context, the firewall attempts to match the packet's destination IP address and TCP/UDP port information with the active translation slots. The context with the corresponding translation slot is chosen as the target context. This categorization allows for the sharing of the same IP subnet or even IP address on the shared interface because translation slots are utilized for traffic categorization, you do not need to have distinct MAC addresses in each context.
- If all contexts on the same interface utilize the same IP address/MAC, you will be unable to access the shared interface because it classifies traffic headed for the firewall depending on the destination IP address. As a result, it is typically suggested to utilize different IP addresses (MAC addresses might be the same) on shared interfaces.
Continue Reading...
- Leveraging Cisco ASA: Modular Policy Framework
- Cisco ASA/ASDM Upgrade procedure
- Cisco ASA Configuration Guide: Step-by-Step VPN Traffic Restriction
- Cisco ASA : Configuring a Hub-and-Spoke IKEv1 IPSec VPN
- Cisco ASA Series 7: Scanning Threat Detection
- Cisco ASA Series 6: Configuring Threat Detection-Advanced
- Cisco ASA Series 5: Configuring Threat Detection
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
More on Cisco ASA...
- Cisco ASA Password Recovery Procedure
- Security: Cisco ASA Vs Cisco FTD
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls
- Site to Site IPSec VPN Tunnel between Cisco ASA and Meraki MX