Cisco ASA Configuration Guide: Step-by-Step VPN Traffic Restriction
Cisco ASA Configuration Guide: Step-by-Step VPN Traffic Restriction
The Cisco ASA security appliance integrates a firewall, antivirus software, intrusion detection, and a virtual private network (VPN) into a single unit. It allows for proactive threat defense, preventing attacks from propagating over the network.
The two LANs are fully network connected by default when using a site-to-site IPSEC VPN. Hosts in LAN1 can thus reach any hosts in LAN2, and vice versa. Still, there are several circumstances in which this would not be acceptable. Sometimes we want hosts from one site to access the full network, while other times we want them to access just certain hosts on the other site.
⭐ CLI Command configuration Scenario 📜
Disabling the default command "sysopt connection permit-vpn" is crucial in this situation. The goal of this command, which is enabled by default on Cisco ASA, is to exclude all IPSEC VPN traffic from the outside Cisco ASA interface's Access List check. This indicates that no restrictions apply to any IPSEC VPN traffic passing between the two sites while the aforementioned command is enabled.
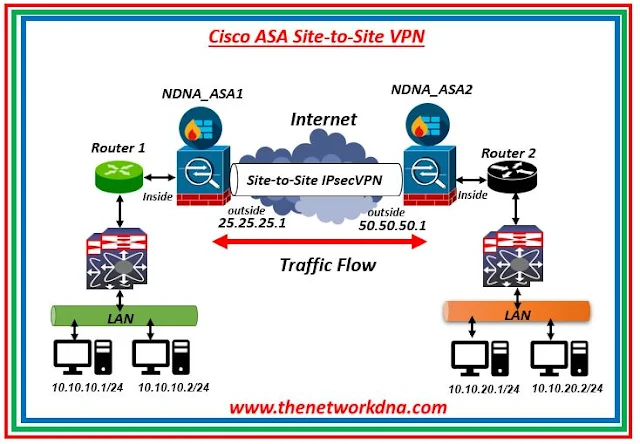 |
| Fig 1.1- Cisco ASA Site-to-Site VPN |
We must specifically permit IPSEC communication from the peer site on the ASA's external Access Control List if we deactivate the aforementioned command. As a result, we are able to implement precise management of the IPSEC communication between the two sites.
IPSEC employs three protocols: ESP, AH, and IKE port UDP 500 (isakmp). As a result, we must provide access to the firewall interface to the protocols indicated in the external Access List. Next, we must explicitly provide access from LAN-2 to certain private hosts on LAN-1.
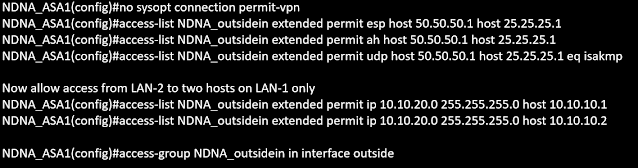
In order to limit LAN-2's access to just two hosts (10.10.10.1 and 10.10.10.2) on LAN-1, let's examine how to restrict IPSEC VPN traffic. On the NDNA_ASA-1, below configuration will be pushed
Continue Reading...
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Cisco ASA Series 2: Configuring NAT
- Cisco ASA Series 3: Easy VPN Remote
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
- Cisco ASA Series 5: Configuring Threat Detection
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls
More on Cisco ASA...