Cisco Secure Firewall: Clustering Basics
Cisco Secure Firewall: Clustering Basics
Clustering allows you to bring together many Firepower Threat Defense devices into a single logical device. Clustering is only available for the Firepower Threat Defense device on the Firepower 9300 and Firepower 4100 models.
A cluster offers all of the benefits of a single device (administration, network integration) while providing enhanced throughput and redundancy from several devices.
⭐Related : Cisco Next Generation Firewalls : Cisco Firepower 9300 Series introduction
⭐Related : Cisco Secure Firewall 7.x
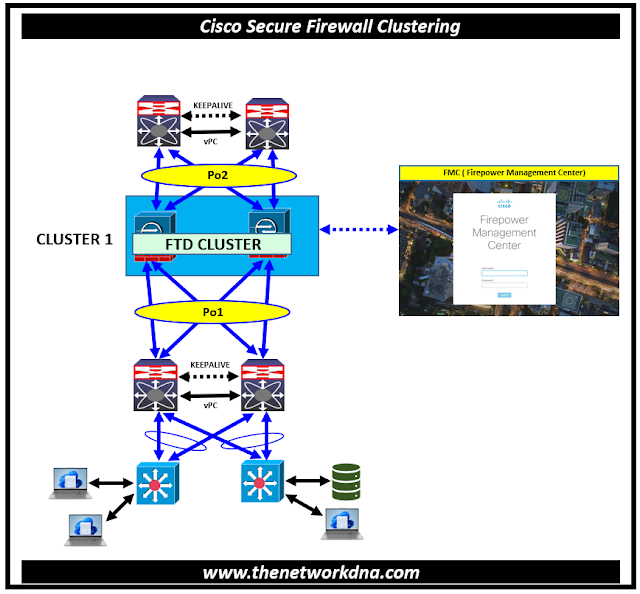 |
| Fig 1.1- Cisco Secure Firewall: Clustering Basics |
⭐ Purpose of Cisco Secure Firewall Clustering
- A cluster provides all the convenience of a single device (management, integration into a network)
- Firewalls must be same models , same modes,
- Active/active, Active/standby. Cisco Secure Firewall 4200 Series allows clustering of up to 8 chassis and Active/active and Active/standby; up to 6 modules across up to 6 different Firepower 9300 chassis In case of ASA you can do up to 16 security modules across up to 16 different Firepower 9300 chassis
- Supported in both physical and virtual cisco secure firewall
⭐ When deploying Cluster on Cisco Firepower 4100/9300 Chassis
- For native instance clustering, establishes a cluster-control link (by default, port-channel 48) for node-to-node communication.
- For multi-instance clustering, you need set up sub interfaces on one or more cluster-type Ether Channels; each instance requires its own cluster control link.
- For a cluster isolated to security modules within a single Firepower 9300 chassis, this link uses the backplane to facilitate cluster communications.
- For clustering with several chassis, you must explicitly allocate physical interface(s) to this Ether Channel for communication between the chassis
Cluster has three nodes that are part of the whole process and these nodes are
- Control Node – synchronizes cluster configuration
- Flow Owner (nondeterministic) – receiver of the first packet of a flow
- Flow Director (deterministic) – keeps track of the flow owner
There is a Cluster Control link running between nodes for communications which helps you provide
- Connection state sharing
- Node discovery and health check
- Asymmetric traffic redirection to the flow owner
⭐ Cluster Operation
- If a node receives a flow's SYN packet, it notifies the flow director that it has become the flow's owner.
- If a node receives a packet that is not a SYN packet and is not part of a flow it owns, it will contact the flow director.
- The flow director answers with the location of the flow owner (if one exists). The node routes the packet through the CCL to the flow owner.
- If the flow director responds that there is no flow owner, the node drops the packet.
We will talk about the configuration related to clustering for Cisco Secure Firewalls in our next article.
Continue Reading...
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Cisco ASA Series 2: Configuring NAT
- Cisco ASA Series 3: Easy VPN Remote
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
- Cisco ASA Series 5: Configuring Threat Detection
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls







