Active/Passive HA Setup in Palo Alto Firewall
Active/Passive HA Setup in Palo Alto Firewall
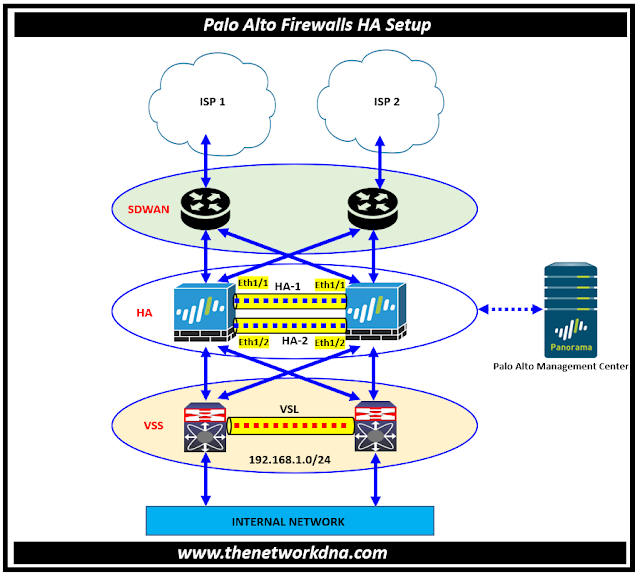
High availability (HA) is a setup in which two firewalls are grouped together and their configurations are synchronized to avoid a single point of failure on your network. A heartbeat connection between firewall peers ensures that if one of them fails, the others can continue to function. Setting up two firewalls in a HA pair ensures redundancy and uninterrupted operations.
As you know that two Palo Alto Networks firewalls can be configured as a HA pair; the HA peers must run the same PAN-OS version and content version.
HA helps to reduce downtime by ensuring that an alternate firewall is accessible in the case that the peer firewall fails. An HA pair's firewalls use dedicated or in-band HA ports to synchronize data network, object, and policy configurations as well as status information.
Peers do not communicate firewall-specific configurations such as management interface IP addresses or administrator profiles, HA configurations, log data, or Application Command Center (ACC) information over the HA.
Fig 1.1- Active/Passive HA Setup in Palo Alto Firewall
A Failover occurs when one of the firewalls in a HA pair fails and the peer firewall assumes responsibility for protecting traffic in the following conditions
- When monitor interfaces fail on the PA firewall.
- When there are some destinations cant be reached through PA firewall.
- When PA firewall not responding to heartbeat polls.
- When packet path health monitoring fails on PA firewall.
⭐Related : IPsec site-to-site VPN tunnel between Palo Alto Firewall & FortiGate Firewall
⭐ Configuring HA setup on Palo Alto Firewalls
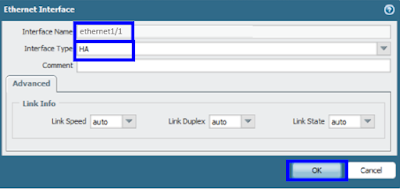
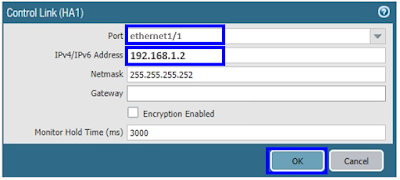
Navigate to General tab >> Control Link section >> click on Primary.
PALO ALTO PA -1
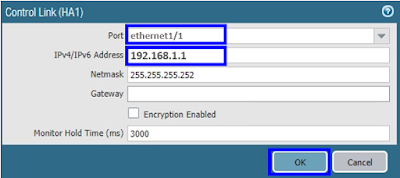
Port for Control Link HA1 : Ethernet 1/1
IP address : 192.168.1.1
Port for Control Link Primary : Ethernet 1/1
IP address : 192.168.1.2
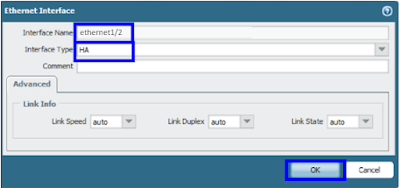
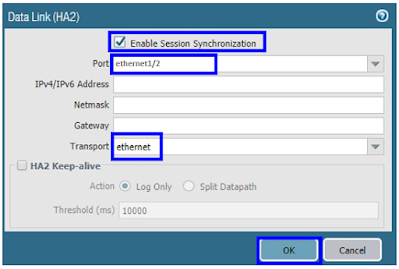
Port for Data Link Primary : Ethernet 1/2
Ethernet1/2 is our HA2 link. It's directly connected, thus the transport method is ethernet. We don't need to mention any IP addresses. However, if your data link is routed over L3 networks, you must give IP addresses.
PALO ALTO PA -1 and PALO ALTO PA -2
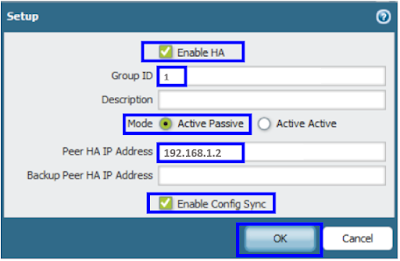
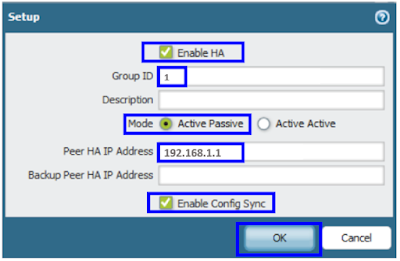
Checkbox for HA: Done
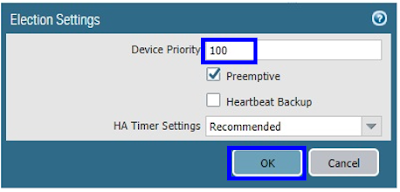
The firewall with the lower numerical value, and therefore higher priority, is designated as active. The other firewall is the passive firewall.
So we need to make Palo Alto PA-1 as Active and Palo Alto PA-2 as Passive
Continue Reading...
- IPsec site-to-site VPN tunnel between Cisco ASA & FortiGate Firewall
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls
- Site-to-Site IPsec VPN Tunnel with two FortiGate Firewalls
- IPsec site-to-site VPN tunnel between Palo Alto Firewall & FortiGate Firewall
- Lan-to-Lan IPSEC VPN between two Cisco Routers
- Security: FortiGate to SonicWall VPN Tunnel setup
- How to configure IPSEC Tunnel configurations between two routers across Internet