Cisco FTD High Availability (HA) requirements and Configuration
Cisco FTD High Availability (HA) requirements and Configuration
Cisco secure firewalls (FTD/NGFW) High Availability (HA) is a feature that enables you to set up two Cisco Firepower Threat Defense (FTD) devices to function as a redundant pair. It means that if one device fails, the other may take over and continue forwarding traffic, reducing downtime and maintaining business continuity.
⭐Related : Cisco Next Generation Firewalls : Cisco Firepower 9300 Series introduction
⭐Related : Cisco Secure Firewall 7.x
Fig 1.1- Cisco Secure Firewalls in HA
- To configure FTD HA, two identical FTD devices must be connected by a dedicated failover link and, optionally, a state link. The same link can be used for both the failover and state links.
- Identical devices means that FTD devices must be the same model with the same interface type and number of interfaces. Software version and Firewall mode must also be the same.
- Over the failover link, the status of each device is monitored, and the configuration is synchronized.
- Connection state information, such as the session table and NAT table, is synchronized across the state link, ensuring that current connections are not disturbed during a failover.
Before we are going with the HA setup between both FTD appliances, first verify that they meet conditions
Step 1: Verify the hardware on both FTDs NDNA-FPR9K-1 and NDNA-FPR9K-2 as shown below
NDNA-FPR9K-1# show server inventory
Server Equipped PID Equipped VID Equipped Serial (SN) Slot Status Ackd Memory (MB) Ackd Cores
------- ------------ ------------ -------------------- ---------------- ---------------- ----------
1/1 FPR9K-SM-36 V01 FLMxxxxxxxx Equipped 262144 36
1/2 FPR9K-SM-36 V01 FLMyyyyyyyy Equipped 262144 36
1/3 FPR9K-SM-36 V01 FLMzzzzzzzz Equipped 262144 36
NDNA-FPR9K-1#
NDNA-FPR9K-2# show server inventory
Server Equipped PID Equipped VID Equipped Serial (SN) Slot Status Ackd Memory (MB) Ackd Cores
------- ------------ ------------ -------------------- ---------------- ---------------- ----------
1/1 FPR9K-SM-36 V01 FLMaaaaaaaa Equipped 262144 36
1/2 FPR9K-SM-36 V01 FLMbbbbbbbb Equipped 262144 36
1/3 FPR9K-SM-36 V01 FLMcccccccc Equipped 262144 36
NDNA-FPR9K-2#
Step 2: Check the software versions on both FTD devices, you can verify that by login to the both the chassis one by one and navigate to Logical devices.
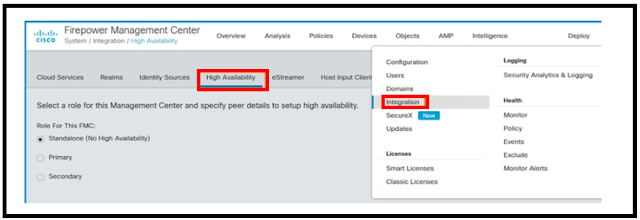
Step 3: To configure FTD failover, click to Devices > Device Management and select Add High Availability
Step 4: Enter device type, Primary Peer and secondary peer to setup the High Availability pair (HA) for both the FTDs.
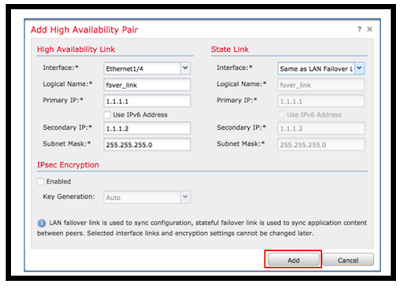
Step 5: Now need to put the HA link configurations and State link configurations
Continue Reading...
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Cisco ASA Series 2: Configuring NAT
- Cisco ASA Series 3: Easy VPN Remote
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
- Cisco ASA Series 5: Configuring Threat Detection
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls