All about SFTP (Secure File Transfer Protocol)
All about SFTP (Secure File Transfer Protocol)
SFTP (Secure File Transfer Protocol, often known as Secure FTP) is a widely used method for securely transmitting data between remote systems. SFTP was created as an extension of the Secure Shell protocol (SSH) version 2.0 to improve secure file transfer functionality.SFTP provides file access, transfer, and management capabilities without the use of command or data channels. Instead, both data and commands are encrypted and transmitted in specially prepared binary packets via a single, secure connection via SSH.
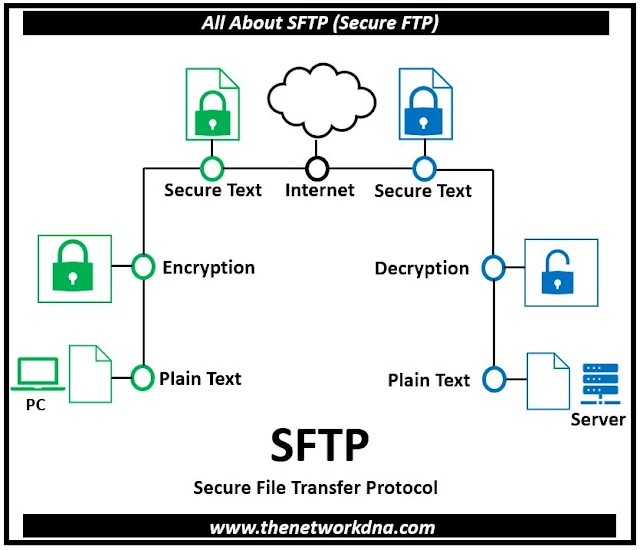 |
| Fig 1.1- SFTP |
They need specific SFTP clients that use SSH to access, manage, and transfer files. The Command-Line Interface (CLI) on UNIX and Mac OS X hosts can be used as SFTP clients. There are also several graphical FTP applications, such as the free FTP client for Windows, FTP Voyager, which allows file transfer via SFTP.
⭐ Benefits of SFTP over FTP & FTPS ⭐
- File transfer is much faster as SFTP transmits data in binary format; therefore, less data crosses the wire compared to FTPS.
- SFTP uses only one connection, and there’s no need for a dedicated data channel.
- The SFTP connection is always secured with SSH.
- The SFTP directory listing is uniform and machine-readable.
- In addition to file transfer, SFTP also includes operations for permission and attribute manipulation, file locking, etc.
⭐ SFTP connection authentication⭐
- Basic authentication requires a user ID and password from the SFTP client user to connect to the SFTP server.
- SSH authentication uses SSH keys to authenticate SFTP connections instead of, or in combination with, a user ID and password. An SSH public key and private key pair are required in this case.
- Generate a key pair on your computer (SFTP client), and copy the public key to the SFTP server.
- When the server authenticates your connection to it, PuTTY generates a signature using your private key.
- The server, which has the matching public key, can verify this signature and authenticate your connection.
Even if the SFTP server is compromised or spoofed, the attacker will only obtain one signature, not your secret key or password. Because signatures cannot be reused, he has gained nothing.
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Cisco ASA Series 2: Configuring NAT
- Cisco ASA Series 3: Easy VPN Remote
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
- Cisco ASA Series 5: Configuring Threat Detection
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls







