Back to Basics: Understand the different types of VPN
Back to Basics: Understand the different types of VPN
⭐Amazon.com Best Deals Toys ⭐Amazon.com Best Deals Health
⭐Amazon.com Best Deals Electronics ⭐Amazon.com Best Deals Video Games
With the rise of cyber risks and privacy concerns, the use of Virtual Private Networks (VPNs) has grown in popularity. VPNs not only allow users to circumvent geographic limitations and access region-locked content, but they also keep their online actions private from prying eyes.
It's critical to understand the fundamental concepts of how a VPN works. A VPN establishes a safe and encrypted link between the user's device and the internet, passing data through an intermediate server.
This method masks the user's IP address and encrypts their online actions, assuring privacy and security. There are various VPN protocols, each with its own set of features, limitations, and applications. IPSec, L2TP, PPTP, SSL, TLS, OpenVPN, and SSH are the most extensively used VPN protocols.
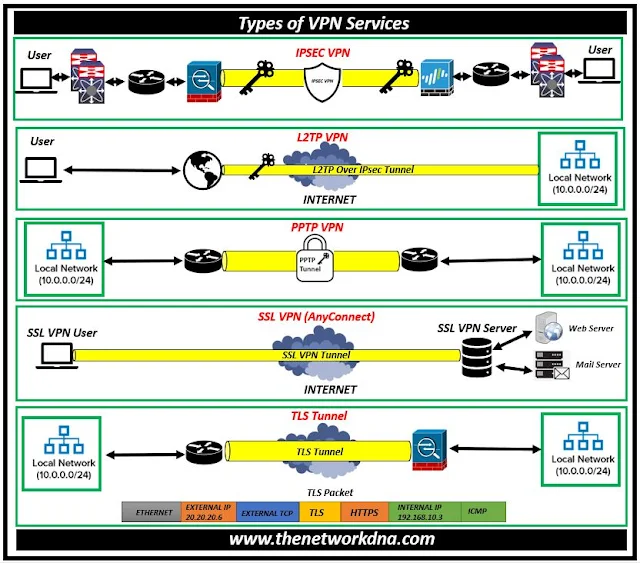 |
| Fig 1.1- Types of VPN |
⭐ IPSec VPN 👇
An IPsec VPN is a type of virtual private network that uses the IPsec protocol to create an encrypted tunnel over the internet. IPSec (Internet Protocol Security) is one of the most extensively used VPN protocols. IPSec runs at the OSI model's network layer and provides strong security features such as encryption, authentication, and data integrity.
IPSec VPNs are appropriate for enterprises and businesses that need a high level of security for remote access and site-to-site communications. However, setting up and configuring IPSec VPNs can be difficult, requiring significant technical knowledge.
IPsec offers data integrity and secrecy through encryption, integrity check, and authentication. IPsec VPNs encrypt data being transferred between the device and the VPN server using a method known as "tunneling." Main features of IPSec tunnel
- Confidentiality – It means encrypt the data.
- Integrity – It ensures that data has not been tampered or altered using hashing
- algorithm.
- Authentication – It confirms the identity of the host sending data, using
- pre-shared keys or CA (Certificate Authority)
- Anti-replay – prevents duplication of encrypted packets
⭐ Related : Understand IPSec protocol
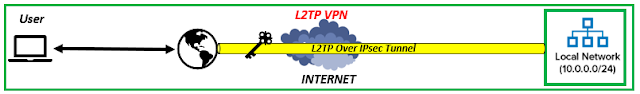
⭐ L2TP VPN 👇
L2TP (Layer 2 Tunneling Protocol) is a VPN protocol that combines the best characteristics of both PPTP and L2F (Layer 2 Forwarding). It offers robust encryption and is well-known for its ability to support numerous protocols.
L2TP is frequently used in conjunction with IPSec to improve security, making it a popular choice for securing sensitive data exchanges. While L2TP provides strong security, the additional encryption overhead may make it unsuitable for consumers who value speed and performance.
So simply, you can say that L2TP VPNs don't offer confidentiality, but they do offer encryption and tunneling. Because of this, L2TP VPNs are frequently combined with IPsec, which offers confidentiality and encryption.
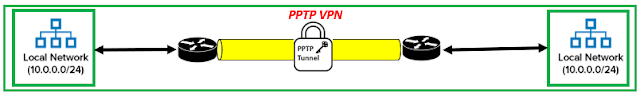
⭐ PPTP VPN 👇
Point-to-Point Tunneling Protocol (PPTP), is renowned for being straightforward and simple to set up. Many users find it to be a convenient option because it is widely supported across multiple platforms and operates at the data-link layer of the OSI model.
Because it can handle high-speed connections, PPTP is preferred for streaming and gaming. Its security credentials have been questioned, though, so users who value privacy and data protection might want to consider other options.
PPTP VPNs communicate over TCP port 1723 and wrap PPP packets using the Generic Routing Encapsulation (GRE) protocol. When a user connects to a PPTP VPN, their device initially establishes an IPSec Security Association (SA) with the VPN server. Following that, the Encapsulating Security Payload (ESP) mechanism for the transport mode is established. Finally, PPTP enters the picture, negotiating and establishing a tunnel between the network endpoints.
⭐ SSL VPN 👇
Web-based VPN, sometimes referred to as Secure Socket Layer (SSL) VPN, offers safe remote access to websites, web apps, and internal network resources. Because SSL VPNs can be accessed through a web browser and don't require the installation of additional software or clients, they provide a user-friendly and intuitive experience.
SSL VPNs are the best option for customers who need to have easy access to corporate resources from any place while maintaining security. SSL VPNs, however, might not be appropriate for resource-intensive applications that need complete network access.
SSL VPNs encrypt traffic between a web browser and an SSL VPN device using the SSL or Transport Layer Security (TLS) protocol. This implies that all transmission between a web browser and an SSL VPN device is encrypted, ensuring data privacy and integrity.
⭐ TLS VPN 👇
Secure network communication is ensured via the cryptographic protocol known as Transport Layer Security (TLS). TLS VPNs provide secure connections between users and the network by utilizing the security features of the TLS protocol.
The TLS VPN protocol is divided into two layers: the TLS Record Protocol and the TLS Handshake Protocol. The TLS Record Protocol ensures the secrecy and reliability of the connection, whereas the TLS Handshake Protocol encrypts your shared data and makes it inaccessible to eavesdroppers, attackers, and other unwanted parties.
TLS VPNs combine strong encryption with comparatively fast connection speeds to create an optimal combination of security and performance. Because of this, a variety of uses, such as VoIP communication, file sharing, and secure remote access, can benefit from TLS VPNs.
⭐ Open VPN 👇
OpenVPN is a popular open-source VPN protocol due to its flexibility, dependability, and robust security features. OpenVPN employs a proprietary security protocol based on the OpenSSL library and is compatible with a wide range of encryption techniques.
OpenVPN's open-source nature allows for continual innovation and refinement, making it a popular choice among many individuals and companies. Because of its ability to quickly bypass firewalls and cross-platform compatibility, OpenVPN is a viable alternative for a variety of use scenarios.
⭐ SSH VPN 👇
SSH VPN is built on the SSH protocol, which is widely used for secure remote access and command-line execution. SSH VPNs provide strong authentication procedures as well as a secure, encrypted channel for data delivery.
SSH VPNs are popular among technical users and system administrators due to their ease of use and efficacy in safeguarding network connections. SSH VPNs, on the other hand, may not provide the same level of user-friendliness and convenience of use as other VPN protocols.
⭐Conclusion
There are several VPN protocols that cater to different needs, whether it be security, speed, ease of use, or flexibility. Understanding the advantages and disadvantages of each VPN type is critical for making an informed decision.
Users can assure a safe and private online experience while benefiting from unfettered access to content and resources by selecting the appropriate VPN protocol.
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Cisco ASA Series 2: Configuring NAT
- Cisco ASA Series 3: Easy VPN Remote
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
- Cisco ASA Series 5: Configuring Threat Detection
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls