Cisco Secure Firewall : Encrypted Visibility Engine (EVE)
Cisco Secure Firewall : Encrypted Visibility Engine (EVE)
Cisco Secure Firewalls deliver enhanced network protection against increasingly complex and evolving threats.
Cisco's security infrastructure is both flexible and integrated, enabling you to provide the strongest security posture possible for today and tomorrow.
Cisco enables you to extend your firewall solution to your existing network infrastructure, so you can deploy world-class security controls everywhere you need them, from your data center to your branch offices to your cloud environments.
You can protect against even the most sophisticated threats by investing in a Secure Firewall appliance today without compromising performance when inspecting encrypted traffic.
Furthermore, Cisco security products can be seamlessly integrated with third-party products, providing a comprehensive portfolio of security products that can be used together to correlate disconnected events, eliminate noise, and stop threats quickly.
⭐Related : Cisco Next Generation Firewalls : Cisco Firepower 9300 Series introduction
⭐Related : Cisco Secure Firewall 7.x
⭐ What is Encrypted Visibility Engine (EVE) ?
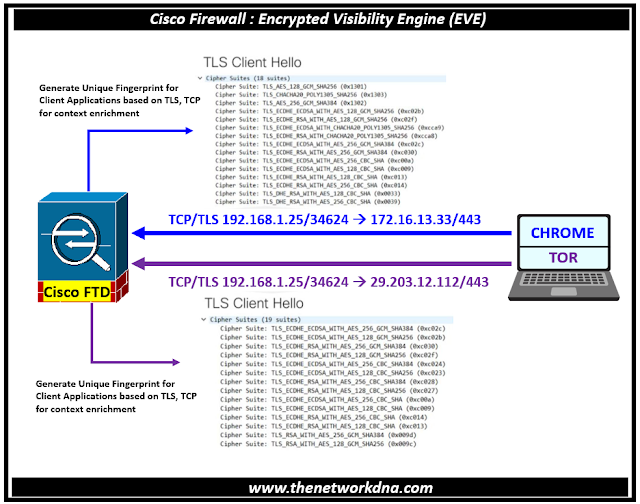
Encrypted Visibility Engine (EVE) is a feature of the Cisco Secure Firewall that improves encrypted traffic inspection without requiring decryption. Encrypted Visibility Engine (EVE) uses Transport Layer Security (TLS) encryption to identify client apps and processes.
Fig 1.1- Cisco Secure Firewall Encrypted Visibility Engine (EVE)
Without decryption, EVE offers greater insight into the encrypted sessions. Administrators can impose policy actions on the traffic in their settings based on the results of EVE. The EVE can also be used to detect and remove malware.
In order to utilize them in access control rules, EVE can map more than 5,000 client processes to client apps. Thus, the firewall doesn't need to decrypt the TLS communication in order to regulate these applications. Using the fingerprints of known dangerous processes, EVE's technology can also assist in detecting and eliminating malware.
⭐ Why we need Encrypted Visibility Engine (EVE) ?
Firewalls are unable to examine encrypted traffic until it has been decrypted; also, NGFW performance is decreased when decryption is enabled. Cisco addresses that by improving encrypted traffic inspection through the use of Encrypted Visibility Engine (EVE), eliminating the requirement for complete main-in-the-middle (MITM) decryption.
Benefits of Encrypted Visibility Engine (EVE)
- Using TLS encryption, EVE is a new method of identifying customer applications and processes.
- It makes information visible, gives administrators the ability to act, and lets them enforce rules in their surroundings.
- The way EVE operates is by using the TLS handshake to fingerprint the Client Hello packet.
- More than 5,000 client processes can be found using EVE.
- EVE is capable of finding and eliminating malware in addition to Firefox and TOR browsers.
- To generate and maintain EVE fingerprints, Cisco analyzes more than 10,000 malware samples and one billion TLS fingerprints per day.
- Customers subsequently receive these updates via packages called Vulnerability Databases (VDBs).
- The threat score that EVE needs in order to block traffic that could be harmful can be changed by administrators.
Continue Reading...
- Security: Cisco ASA Vs Cisco FTD - The Network DNA
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Trunk Port
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration
- Cisco ASA Series 2: Configuring NAT
- Cisco ASA Series 3: Easy VPN Remote
- Cisco ASA Series 4: Configuring VLANs and Sub interfaces
- Cisco ASA Series 5: Configuring Threat Detection
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls