Cybersecurity : DLL hijacking in 8 Steps
Cybersecurity : DLL hijacking in 8 Steps
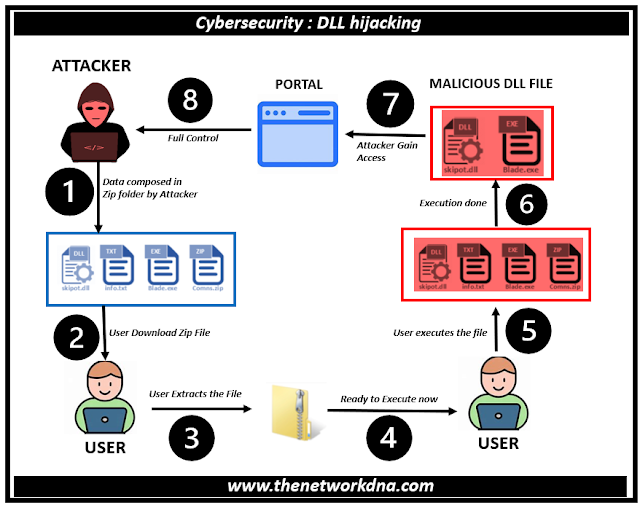
Attackers can swap out authentic dynamic-link libraries (DLLs) for their own malicious versions by using a harmful technique called DLL hijacking. Common UI components and system services are among the shared functionality that these DLLs are responsible for supplying and are an integral part of every Windows-based application.
Hackers can potentially gain complete control over Green c Computer Systems by inserting malware into applications through the replacement of these DLLs.
DLL hijacking has its origins in the earliest versions of Windows. But this assault is more common and dangerous than it has ever been because so many contemporary software programs rely heavily on DLLs. In fact, DLL hijacking is one of the top 25 most serious software security threats according to the U.S. Department of Homeland Security.
Because DLL hijacking is such a subtle strategy, users frequently miss it. The impacted program may carry on as normal after a hacker successfully changes a valid DLL, providing no obvious signs of the underlying malicious behavior. Because of its clandestine nature, cybercriminals who want to go unnoticed often use it as a method.
Consequences DLL Hijacking
DLL hijacking can have serious effects, such as system compromise and data theft. When a hijacking attempt is successful, the attacker frequently has the same rights as the compromised program to run arbitrary code.
- Theft of data and illegal access to private data
- installation of malicious software, including ransomware and keyloggers
- altering configuration files and system settings
- Downtime and disturbance of server operations
Detecting DLL Hijacking
Although identifying DLL hijacking can be difficult, security experts and companies can use the following techniques to spot such threats:
- Monitor application logs on a regular basis for strange activity, such as failed searches for DLLs in unexpected locations or issues when loading DLLs.
- Advanced behavioral analysis techniques can discover anomalies in DLL usage patterns and highlight dubious behavior.
- On the daily basis, do check the vulnerability test
- Also trying to implement the network segmentation in your network in order to avoid compromised DLL impact
Preventing DLL Hijacking
To save you DLL hijacking, companies can adopt the following measures:
- Ensure that packages are configured to look for DLLs in secure and predicted locations, which includes the utility's directory or the Windows system listing
- Utilize sturdy protection policies and permissions to restriction access to sensitive DLL documents, stopping unauthorized customers from changing them
- Regularly update and patch software program to cope with any recognized vulnerabilities and save you exploitation by way of hijackers
- Implement application whitelisting, a security method that simplest lets in depended on programs to run on a system, greatly lowering the threat of malicious DLLs being achieved
Continue Reading...
- How to Make Your Computer Less Prone to Potential Threats
- Offensive vs. Defensive Security: Which Strategy is Right for You?
- How to Protect Your Data: 10 Best Practices to Defend Against Ransomware
- Securing Open Source Code Repositories Against Exfiltration Attacks
- Top 8 Cyberattacks in 2024
- Top 10 Cybersecurity Vendors in Q1 2024