Top 8 Cyberattacks in 2024
Top 8 Cyberattacks in 2024
A cyberattack is any offensive operation directed at computer systems, computer networks, infrastructures, personal computer devices, or cellphones. The attacker, whether a people or a process, tries to access data, functions, or other restricted parts of the system without authority, frequently with threatening intent.
 |
| Fig 1.1- Top 8 Cyberattacks in 2024 |
There are list of the top 8 Cyberattacks we are going to discuss and you need to prevent yourself with these attacks.
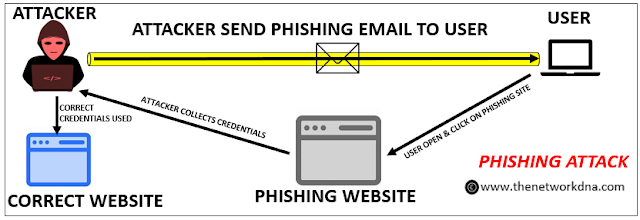
1. Phishing Attack
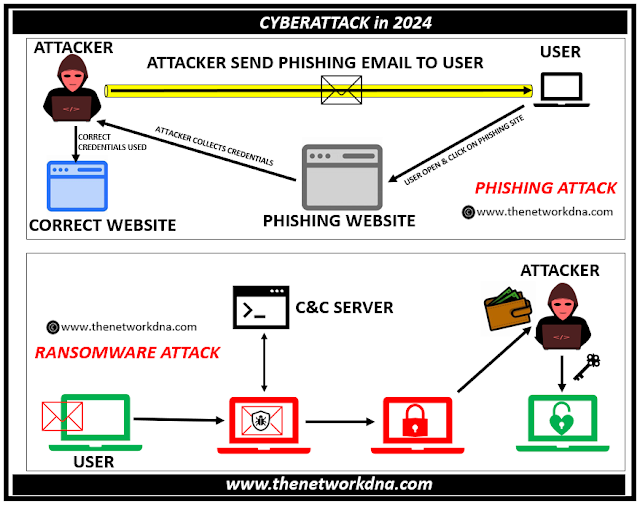
Phishing attacks are the practice of delivering false messages that appear to be from a legitimate source. It is normally done by email. The purpose is to steal sensitive data, such as credit card and login information, or to install malware on the victim's computer. Phishing is a popular sort of cyber attack that everyone should understand in order to defend themselves.
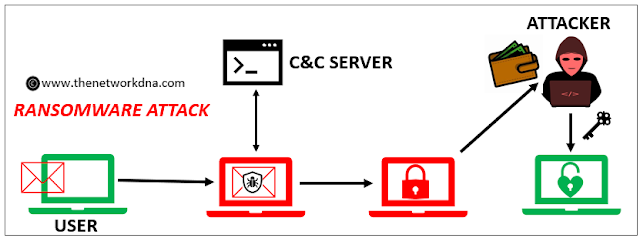
2. Ransomware Attack
A ransomware attack is a type of malware attack in which an attacker locks the user's files, folders, or entire device until a 'ransom' cost is paid. These attacks exploit security weaknesses by infecting a computer or network via phishing attacks or malicious websites.
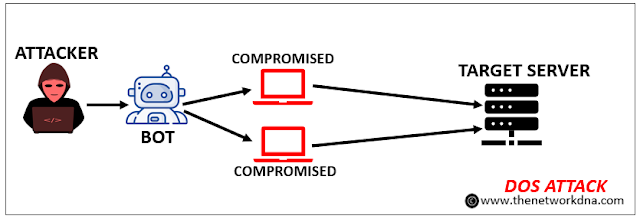
3. Denial-of-Service (DOS)
A denial-of-service (DoS) attack is a sort of cyber attack in which a malicious actor attempts to make a computer or other device unavailable to its intended users by disrupting its usual operation. DoS attacks normally work by flooding a targeted system with requests until normal traffic cannot be processed, causing denial-of-service to other users. A DoS attack is defined as one that is launched from a single computer.
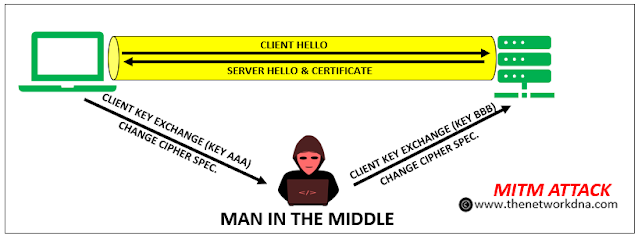
4. Man in the Middle attack (MITM)
A man-in-the-middle (MITM) attack is a type of hack in which attackers use weak web-based protocols to place themselves between entities in a communication channel and steal data.
None of the people sending emails, messaging, or speaking on a video call are aware that an attacker has inserted themselves into the conversation and is taking their information.
While most cyberattacks are stealthy and take place without the victims' knowledge, some MITM attacks are the contrary. They could include a bot sending realistic text messages, imitating a person's voice on a phone conversation, or spoofing an entire communications system to extract data from participants' devices that the attacker considers significant.
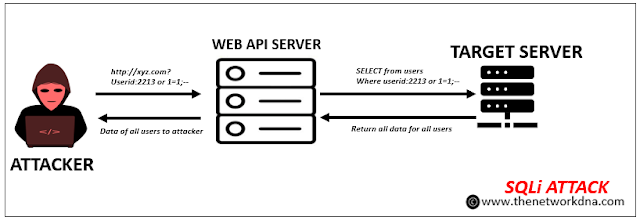
5. SQL Injection (SQLi)
SQL injection (SQLi) is a web security vulnerability that allows an attacker to tamper with an application's database queries. This allows an attacker to view data that they would not normally be able to access. This may include data belonging to other users or any other data that the application has access to. In many circumstances, an attacker can modify or remove this data, creating long-term changes to the application's content or behavior.
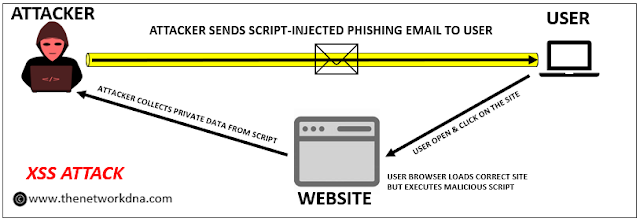
6. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a code injection attack in which an adversary inserts malicious code into a legitimate website. The code then executes as an infected script on the user's web browser, allowing the attacker to obtain sensitive information or impersonate the user.
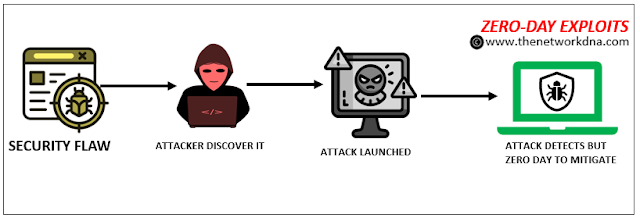
7. Zero-Day Exploits
A zero-day exploit is a cyberattack route that takes use of an undiscovered or unpatched security hole in computer software, hardware, or firmware. The term "zero day" refers to the fact that the software or device vendor has zero days to remedy the hole since malicious actors have already exploited it to get access to vulnerable systems.
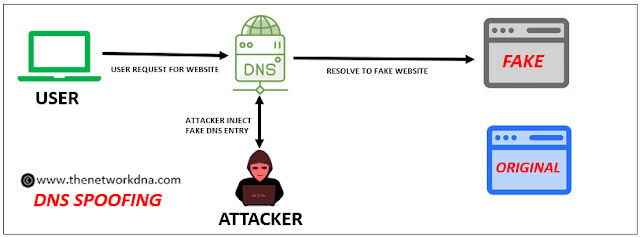
8. DNS Spoofing
Domain Name Server (DNS) spoofing, also known as DNS cache poisoning, is an attack in which DNS records are manipulated to redirect visitors to a false, malicious website that may look like the user's intended destination.
Once on the fraudulent site, users are tricked into checking in to what they assume to be their legitimate account, allowing the attacker to obtain access passwords or other sensitive data. The bogus website might secretly install worms or viruses on the user's computer, granting the attacker long-term access to the device and data.
Continue Reading...