Enterprise App Aware Firewall in Cisco SDWAN
Enterprise App Aware Firewall in Cisco SDWAN
⭐Amazon.com Best Deals Toys ⭐Amazon.com Best Deals Health
⭐Amazon.com Best Deals Electronics ⭐Amazon.com Best Deals Video Games
To understand the Cisco SDWAN's Enterprise App aware firewall you need to understand the zone-based model to inspect and control traffic based on applications or application families.
When data traffic flows are matched using any of the six available match criteria (Source port, destination port, protocol, application/application family, and source data prefix) on the vManage security policy dashboard, the Enterprise Firewall with App Aware policy, a localized security policy, enables stateful inspection of those flows.
⚡ Related : Cisco SD-WAN App-aware SLA Based routing in Action
⭐ What is a Zone ? 👇
A collection of one or more VPNs is called a zone. You may create security boundaries in your overlay network and regulate the flow of all data traffic across zones by grouping VPNs into zones.
- The collection of VPNs known as the source zone is where the data traffic flows begin.
- The collection of VPNs known as the destination zone is where the data traffic flows end.
- A firewall policy is a type of localized security policy that specifies the requirements that must be met by data traffic flowing from the source zone to the destination zone.
- In a zone pair, a source zone and a destination zone are linked, and any traffic that moves between them is subject to a firewall policy.
⭐ Cisco SDWAN: App Aware Firewall Zones 👇
The Enterprise App Aware Firewall is further split into Intra zone-based security and Inter-zone-based security depending on the traffic flow across zones.
- Intra-zone based security: An intra zone firewall is one that controls traffic flow between two zones that are connected to the same VPN.
- Inter-zone based Security: An inter-zone firewall is used to control traffic flow between two different zones connected to separate VPNs.
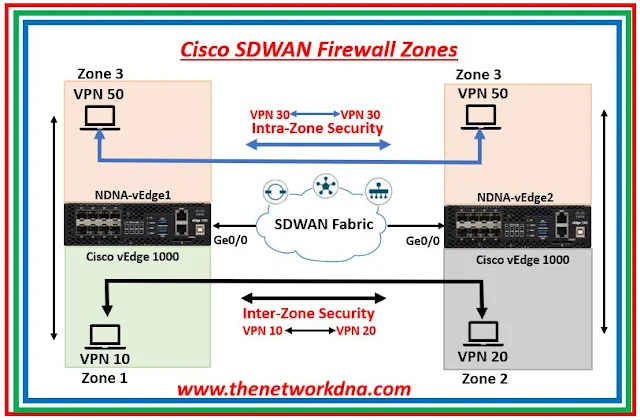 |
| Fig 1.1- Cisco SDWAN Firewall Zones |
Traffic flows from one zone to another are allowed or not allowed, it depends on the policy match and action requirements of that zone.
- Create zones and set firewall rules between them to organize VPNs into security boundaries.
- Match traffic flows and accept, discard, or prohibit them depending on IP prefixes, ports, protocols, and applications.
- Examine packet headers for source and destination addresses and ports while doing stateful inspection of TCP, UDP, and ICMP data traffic flows.
- Sort more than 1400 layer 7 apps, then use application or application family classification to prevent flow.
- Cisco SD-WAN Manager and Cisco SD-WAN Analytics, monitors on firewall data and logs.
⭐ Firewall Policy: Matching Conditions 👇
- Inspect: The Enterprise Firewall with Application Aware policy monitors the flow conditions and establishes sessions when the action is set to Inspect. Return traffic is permitted since it preserves the status of the flows, therefore no additional policy has to be configured for it.
- Pass: Traffic from one zone to another can be forwarded by the router when the pass action is configured, the firewall does not generate sessions since it does not monitor the flow status. Traffic is limited to one direction when there is a pass action.
- Drop: Once packets meet the specified match parameters and the action is configured to drop. We're going to drop that packet.
Continue Reading...
- Cisco ASR 1001-HX router as SDWAN router - The Network DNA
- Cisco ASR 1002-X router with NAT64 configurations - The Network DNA
- Cisco ASR 1002-X Basics - The Network DNA
- Cisco ASR 1000: CEF load Balancing Issue and Possible Solution
- Cisco Launches Cisco Catalyst 8000 Edge Platforms : SASE ready, SDWAN enabled
- Downgrade IOS-XE SD-WAN to IOS-XE - The Network DNA
- Redefining Connectivity with new Cisco Services Edge Platform
- Cisco SDWAN Resources - The Network DNA
- Cisco ASR 1001-X Router
- Cisco ASR Compare models- Hardware Comparison ( ASR 1000 Series feature set comparison)
- Cisco SD-WAN: Underlay Network vs Overlay Fabric
- Cisco SDWAN: TLOC & TLOC Carrier
- Cisco SDWAN: Breaking Down Communication Between TLOC Colors
- Cisco Viptela SDWAN: Packet Duplication
- Unify Your Remote Access with Cisco SD-WAN
- Port Channel on Cisco Catalyst 8300 SDWAN devices
- Cisco Viptela SDWAN: Part 1 Migration from vEdges to Catalyst 8500/8300 Routers
- Cisco SDWAN: Reset IOS-XE SDWAN router
- Finding the Right SD-WAN Vendor for Your Business







