Cisco ISE upgrades, Issues and Tips
Cisco ISE upgrades, Issues and Tips
Cisco ISE stands for Identity Services Engine (ISE) policy server and is RADIUS-based, which enables Cisco to support authentication in heterogeneous network infrastructure environments.
Cisco ISE is a network access control and policy enforcement solution that is identity-based. It serves as a unified policy engine for business endpoint access control and network device administration.
Cisco ISE allows you to create and enforce security and access controls for endpoint devices connected to your organization's routers and switches.
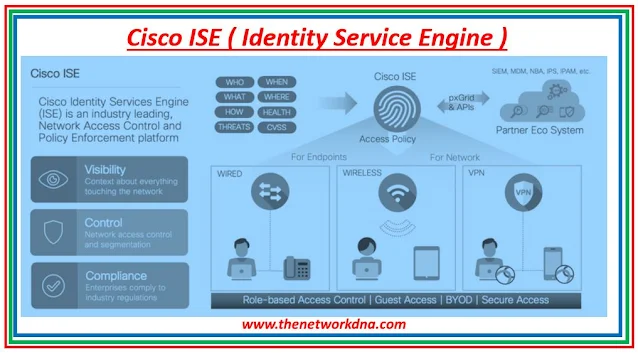 |
| Fig 1.1- Cisco ISE |
Cisco Identity Services Engine (ISE) 1.0
Cisco Identity Services Engine (Cisco ISE) 1.0 is a network security system that offers identity-based access control and security policy enforcement via wired, wireless, and VPN connections.
It was the Cisco ISE platform's first iteration, and it provided the fundamental features for network access control, security posture assessment, and security policy administration. To assist enterprises in securing their networks and devices, Cisco ISE1.0 provides unified identity management and policy enforcement.
Although Cisco ISE 1.0 has been superseded by succeeding versions, it was an important step forward in providing enterprises with identity-based security solutions and helped establish the groundwork for the Cisco ISE platform.
Cisco Identity Services Engine (ISE) 2.0
Cisco Identity Services Engine (Cisco ISE) 2.0 is a network security technology that provides authentication, authorization, and accounting (AAA) services to assist enterprises protect network access.
It unifies wired, wireless, and VPN access security by centralizing identity management, policy enforcement, and posture evaluation. To safeguard the organization's network and devices, the Cisco ISE 2.0 platform provides expanded capabilities for network access control, network security policy administration, and security posture evaluation.
Cisco Identity Services Engine (ISE) 3.0
Cisco Identity Services Engine (Cisco ISE) 3.0 is the most recent version of Cisco's network security technology, which offers identity-based protection for wired, wireless, and VPN connections. It provides powerful network access control, security posture assessment, and security policy management features.
Cisco ISE 3.0 expands on earlier versions' functionality by adding cloud-based identity management, enhanced device profiling, and interaction with other security systems. The purpose of Cisco ISE 3.0 is to assist enterprises in more effectively and efficiently securing their networks and devices while offering a seamless user experience.
Cisco ISE Upgrade Common Issues
Issue 1
EST 2.4 ISE After upgrading from 2.3, the service is no longer operational.
This has been addressed in ISE 2.4 patch 2. A workaround is to rebuild the ISE Root CA chain.
Issue 2
Behind the IP phone is an ISE 2.4 Windows PC characterized as Cisco-IP-Phone. This occurs following an upgrade from ISE 2.2.
This is fixed in the most recent ISE 2.4 patch 4 and the most recent ISE 2.2 patch. So if you dont want to upgrade to ISE 2.4 then you have a workaround to prevent the PC from going down that profiling road, disable the CDP conditions in Cisco-Device. Re-profile the device so that it is properly profiled.
Issue 3
The 35x5 appliance's re-imaging using ISE 2.4 fails. ISE 2.3 is fully functional.
"HTML based KVM" had known issues with CIMC 3.0.3(S2) that is resolved in 4.0(1c).
You have a Workaround and that is use HTML based KVM.
Issue 4
Upgrade from 2.2 to 2.3 fails on UPS schema upgrade step. Exceptions in dbupgrade-liquibase-schema-*.log
This has been addressed in ISE 2.4 patch 2. Hotfixes are required for all other releases.
Issue 5
Because new DNAC pxGrid with ISE fails, ISE2.4 will maintain the old DNAC client cert.
This has been addressed in ISE 2.4 patch 2. A workaround is to erase outdated DNAC client certification.
Issue 6
Upgrade to ISE 2.3: Because of a data replication flaw, monitoring dashboards and reports in a multi-node deployment with Primary and Secondary PANs may fail after the update. Details may be found in CSCvd79546.
You have a workaround for that, before beginning the update, do a manual synchronization from the Primary PAN to the Secondary PAN.
Cisco ISE Tips
- In any of the virtual environments, Cisco ISE does not enable VM snapshots for backing up ISE data.
- To avoid database damage, use the "application stop" command before using the "halt" command or turning off the VM.
- Cisco ISE enables both hot and cold migration (also known as live migration or vMotion).
- When creating a password for the administrator during or after installation in the CLI, do not use the $ character unless it is the last character of the password. The password is acceptable if it is the first or one of the succeeding characters, but it cannot be used to log in to the CLI.
- To boot a GPT partition with 2 TB or more, you must change the firmware from BIOS to EFI in the boot mode of the VM settings.
- When Cisco ISE virtual appliances are deployed using OVF templates, enough resources are assigned to each VM. If you do not utilize OVF templates (you can manually deploy Cisco ISE using the .iso image if you need to customize the disc size, CPU, or RAM allocation), be sure you allocate the appropriate resource reservations when you manually install Cisco ISE using the ISO image.
- Cisco ISE 2.0 Vs Cisco ISE 3.0 - The Network DNA
- Comparing Cisco ACS and Cisco ISE - The Network DNA
- Network Access Control (NAC) - Cisco ISE Vs HPE Aruba Clearpass
- Verify TACACS between Cisco ISE and Cisco DNA center
- Basics about Cisco ISE
- Add ISE as a RADIUS Server for Wired 802.1X
- Cisco ISE & Nodes - The Network DNA







