Cisco Umbrella IPSec tunnel with Fortinet
Cisco Umbrella IPSec tunnel with Fortinet
Fortinet and Cisco Umbrella offer a powerful combination of features to protect your network from malicious threats. With this solution, you’ll be able to quickly identify and contain threats, ensuring your data is safe and secure. Now, you can rest easy knowing your data is secure and your network is protected.
 |
| Fig 1.1-Cisco Umbrella IPsec Tunnel with Fortinet |
You can do this by setting up interoperable site-to-site IPsec tunnels between Fortinet and Cisco Umbrella. By combining Fortinet’s advanced security capabilities with Cisco Umbrella’s comprehensive threat protection, you’ll have a robust solution to ensure your data is safe and secure. Here’s how you can service chain traffic from Fortinet to Cisco Umbrella to enable threat protection
💻 Table Of Content
- Benefits of the Cisco Umbrella and Fortinet Solution
- Configuring IPsec on Cisco Umbrella
- Configuring the Fortinet Primary IPSec Tunnel
- Configuring a Secondary IPSec Tunnel
- Creating Firewall Policies with Fortinet
1. Benefits of the Cisco Umbrella and Fortinet Solution
Advanced threat protection: The Cisco Umbrella and Fortinet solution provides advanced threat protection that can detect and contain malicious activity before it has a chance to cause any damage.
Easy to use: The solution is designed to be easy to use, so you can set it up quickly and get back to business.
Secure data: The Cisco Umbrella and Fortinet solution will ensure your data is secure, so you can rest easy knowing your confidential data is safe.
2. Configure IPsec on Cisco Umbrella
Step 1: Navigate to Deployments > Core Identities > Network Tunnels
Start your journey by navigating to the Deployment page within Cisco Umbrella, and then select Core Identities > Network Tunnels. Once you're there, click "Add" to get started.
Step 2: Select the Appropriate Device Type and Service Type
You'll be prompted to give the Tunnel a name, and then you'll need to select the type of device you're using from the drop-down menu. For the Service Type, select Secure Internet Access.
 |
| Fig 1.2-Cisco Umbrella IPsec Tunnel |
Step 3: Configure the Tunnel ID and Passphrase
In the Configure Tunnel ID and Passphrase section, select FQDN for the Authentication Method, name your Tunnel, and create a passphrase. Then enter the same passphrase again in the Confirm Passphrase field. Once Cisco Umbrella confirms your passphrase, copy and save the Tunnel ID and Passphrase for future reference.
 |
| Fig 1.3-Umbrella to Fortinet IPsec Tunnel |
Step 4: That's It!
You're all set. You can now enjoy secure internet access with Cisco Umbrella
3. Configuring the Fortinet Primary IPSec Tunnel
Setting up a secure connection between your network and the Cisco Umbrella SIG data center is essential for keeping your data and devices safe. Thankfully, configuring the Fortinet Primary IPSec Tunnel is a straightforward process.
Here's a step-by-step guide to help you get up and running quickly:
Step 1 Navigate into Fortinet and Navigate to VPN > IPSec Tunnels
The first step is to log into your Fortinet account and navigate to VPN > IPSec tunnels. This will take you to the main configuration page for the tunnel.
Step 2: Create a New Tunnel
Once you're at the configuration page, select the option to Create New > IPsec Tunnel. Give your tunnel a name and select the template type “Custom”.
Step 3: Configure the Network Settings
The next step is to configure the network settings. You'll need to specify the IP version, remote gateway, IP address (the Cisco Umbrella SIG data center IP address), interface, NAT traversal, and more.
 |
| Fig 1.4 -Fortinet Primary IPSec Tunnel |
Step 4: Set the Authentication Method
In the authentication section, choose Pre-shared Key as the method and add the key. Select IKE Version 2.
 |
| Fig 1.5 -Fortinet Primary IPSec Tunnel |
Step 5: Complete the Phase 1 Proposal
- Encryption: AES256
- Authentication: SHA256
- Diffie-Hellman Groups: 20 and 19
- Key Lifetime (seconds): 86400
- Local ID:
Step 6: Complete the Phase 2 Selectors
The final step is to complete the Phase 2 selectors. You'll need to specify the following:
- Name
- Local Address
- Remote Address
- Encryption
- Authentication
- Enable Replay Detection
- Enable Perfect Forward Secrecy (PFS)
4. Configuring a Secondary IPSec Tunnel
Setting up a secure, encrypted connection between two different networks is no small feat, but luckily, it’s not as complicated as it sounds. In this blog post, we’ll walk you through the process of configuring a secondary IPSec tunnel using Fortinet.
Step 1: Log in to Fortinet and Navigate to VPN > IPsec Tunnels
The first step is to log in to your Fortinet account and then head over to the VPN tab. From there, you’ll need to select the “IPsec Tunnels” option.
Step 2: Create a New IPsec Tunnel
Now, it’s time to create a new IPsec tunnel. Simply click on “Create New” and then select “IPsec Tunnel.” Give your tunnel a name (you can be creative here!) and then select “Custom” as the template type.
Step 3: Enter Network Parameters
The next step is to enter the network parameters. This includes the IP version, the remote gateway, the IP address (the Cisco Umbrella SIG data center IP address), the interface, and the NAT traversal.
 |
| Fig 1.8 -Fortinet Secondary IPSec Tunnel |
Step 4: Select the Authentication Method
In the authentication section, you’ll need to choose “Pre-shared Key” as the method and then enter the key. Make sure you also select IKE version 2.
 |
| Fig 1.9 -Fortinet Secondary IPSec Tunnel |
Step 5: Complete the Phase 1 Proposal
The next step is to complete the Phase 1 Proposal. This includes parameters such as encryption (AES256), authentication (SHA256), Diffie-Hellman groups (20 and 19), key lifetime (seconds) (86400), and local ID.
 |
| Fig 2.1- Fortinet IPsec Phase 1 Proposal |
Step 6: Complete the Phase 2 Selectors
The final step is to complete the Phase 2 Selectors. This includes the name, the local address, the remote address, the encryption, the authentication, enabling replay detection, and enabling Perfect Forward Secrecy (PFS).
 |
| Fig 2.2- Fortinet Phase 2 Proposal |
And there you have it! You’ve just configured a secure secondary IPSec tunnel using Fortinet. You can now rest assured that your networks are safely connected and encrypted.
5. Creating Firewall Policies with Fortinet
Step 1: Create a Policy for the Primary Tunnel
Start by navigating to Policy & Objects > Firewall Policy. Click "Create New" to get started. You'll then need to add the Incoming Interface, Outgoing Interface, Source, Destination, and other details.
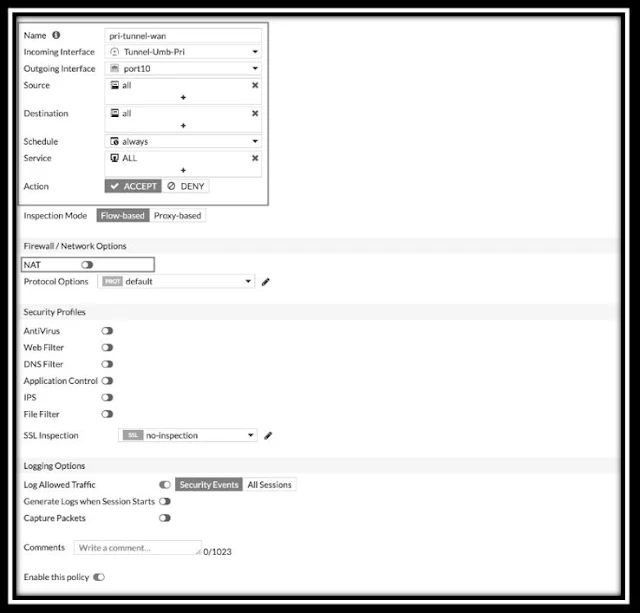 |
| Fig 2.3- Fortinet Object Policy |
Step 2: Create a Policy for the Secondary Tunnel
Repeat Step 1 for the secondary tunnel. Again, you'll need to add the Incoming Interface, Outgoing Interface, Source, Destination, and other details.
Step 3: Finalize Your Firewall Policies
Now, navigate back to Policy & Objects > Firewall Policy and click "Create New" to add the details for the secondary tunnel. Once you've added all the details, your firewall policies will be in place and you're ready to go!
And You're Done!
Continue Reading...
- DNS Security over Cisco SDWAN : Cisco SDWAN Integration with Cisco Umbrella
- IPsec site-to-site VPN tunnel between Palo Alto Firewall & FortiGate Firewall
- IPsec site-to-site VPN tunnel between Cisco ASA & FortiGate Firewall
- DNS Security & Proxy: Cisco Umbrella but Why?
- Compare Zscaler Web Security and Cisco Umbrella: Which is Best?
- Cisco Security : Open DNS ( Cisco Umbrella )
- Leveraging FortiNAC to Strengthen Compliance with Industry Regulations
- Securing Your Network: Cisco Umbrella IPSec Tunnels with Palo Alto Prisma SDWAN








