Securing Your Network: Cisco Umbrella IPSec Tunnels with Palo Alto Prisma SDWAN
Securing Your Network: Cisco Umbrella IPSec Tunnels with Palo Alto Prisma SDWAN
Palo Alto Prisma SDWAN and Cisco Umbrella provide robust security for your internet-bound traffic. Prisma SDWAN ensures that your application traffic flows securely from branch offices over disparate links to data centers, as well as direct-to-internet flows for SaaS applications and general internet usage.
💻 Table of Content
- What is Palo Alto Prisma SDWAN?
- What is Cisco Umbrella ?
- Palo Alto Prisma SDWAN integrate with Cisco Umbrella
- Configure Tunnel in Cisco Umbrella
- Configure Tunnel in Palo Alto Prisma SDWAN
- Configure the Prisma Service Endpoint Group
- Configure the IPsec Tunnel
- Configure the Prisma SDWAN Path Policy
- Conclusion
1. What is Palo Alto Prisma SDWAN?
Palo Alto Prisma SDWAN (Software-Defined Wide Area Networking) is a cloud-based networking solution that enables enterprises to securely and efficiently connect and manage their branch sites, remote users, and cloud resources.
Prisma SDWAN enables enterprises to optimize their WAN traffic and prioritize key applications by providing end-to-end network visibility, application awareness, and management. It creates a virtual overlay network by combining numerous internet lines and secure VPN tunnels to allow seamless communication between branches, data centers, and cloud services.
Prisma SDWAN also incorporates extensive security features, such as a next-generation firewall and threat prevention capabilities, to safeguard WAN traffic from cyber attacks. It detects and prevents sophisticated attacks in real time using machine learning and behavioral analytics.
The system is cloud-delivered, which means it can be rapidly and simply implemented and is constantly up to date with the most recent security features and fixes. Prisma SDWAN also comes with a centralized management panel, which gives managers a unified view of the network and allows them to setup and administer rules and security settings from a single spot.
2. What is Cisco Umbrella ?
Cisco Umbrella is a cloud-delivered security service that provides protection against internet threats such as malware, phishing, and ransomware. It offers DNS and IP-layer security, which allows it to block requests to malicious domains and IPs before a connection is established.
Cisco Umbrella works by redirecting DNS requests to its global network of servers, which perform real-time analysis of the request to determine if it is safe or not. If the request is deemed unsafe, Cisco Umbrella blocks it, preventing the user from accessing the malicious site or downloading malware.
In addition to protecting users from internet threats, Cisco Umbrella also provides visibility into internet activity across an organization's network. It can track internet usage across devices and locations, giving administrators the ability to enforce security policies and prevent unauthorized access.
Cisco Umbrella is designed to be easy to deploy and manage, making it a popular choice for organizations of all sizes. It can be integrated with other Cisco security solutions, such as Cisco Secure Firewall and Cisco Secure Email, to provide comprehensive security coverage.
3. Palo Alto Prisma SDWAN integration with Cisco Umbrella
Enforced Security Protocols: Per-application policy enforcement of application traffic flows ensures that each application is handled with the appropriate security protocols.
Advanced Threat Prevention: Cisco Umbrella's advanced threat prevention helps protect organizations from malicious actors, such as malware, ransomware, and phishing.
Proactive Protection: Cisco Umbrella's proactive protection is designed to scan the internet for malicious websites and block them before they reach your network.
4. Configure Tunnel in Cisco Umbrella
Step 1: Navigate to Deployments > Core Identities > Network Tunnels and click Add.
Step 2: Give your tunnel a meaningful name and choose Others from the Device Type drop-down.
Step 3: Select Secure Internet Access for Service Type.
 |
| Fig 1.2- Cisco Umbrella Secure Internet Access |
Step 4: Select Fully Qualified Domain Name (FQDN) or IP Address/Network for the Authentication Method. Add the Tunnel ID and create a passphrase.
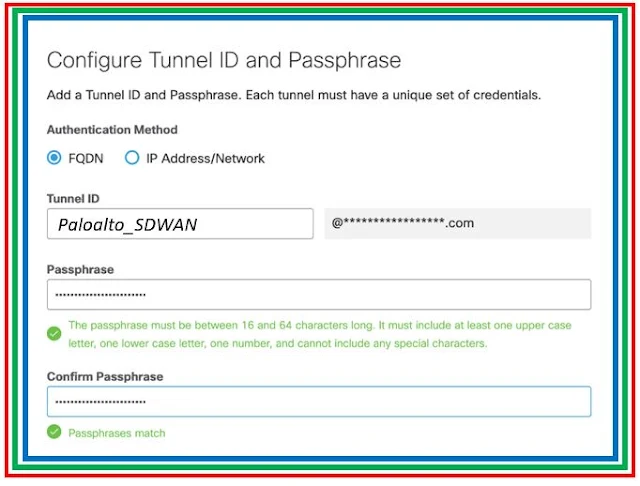 |
| Fig 1.3-Cisco Umbrella Tunnel to Prisma SDWAN |
Step 5: Copy the Tunnel ID and passphrase and save for Configure the Prisma IPsec Profile.
5. Configure Tunnel in Palo Alto Prisma SDWAN
Step 1: In Prisma SDWAN, navigate to Policies > Stacked Policies, click IPsec Profiles, and click Add IPsec Profile.
Step 2: Enter the IKE Group settings to align with Cisco Umbrella's Supported IPsec Parameters and click Next
Step 3: Enter the ESP Group settings to align with Cisco Umbrella's Supported IPsec Parameters and click Next.
Step 4: Set the Authentication Type to None and click Next. Now review and verify the configuration and click Save and Exit.
6. Configure the Prisma Service Endpoint Group
Step 1: In Prisma SDWAN, navigate to Policies > Stacked Policies, click Service & DC Groups, and click Endpoints.
Step 2: Select Standard VPN from the Prisma SDWAN drop-down.
Step 3: Click Add Endpoint, enter a meaningful name and optional description, and then click IPs & Hostnames.
Step 4: Enter the Cisco Umbrella IPsec head-end IP(s) that are desired for this endpoint. Click Done and Save & Exit.
Step 5: In the Groups tab, click Add and select Standard VPN.
7. Configure the IPsec Tunnel
Step 1: In Prisma SDWAN, navigate to Map > Claimed Devices, and click the device where the IPsec tunnel will be configured.
Step 2: Click the Interface configuration tab, click the "+" icon to add an interface, select Standard VPN, and then click Add.
Step 3: Configure the tunnel with Name, Interface Type, Standard VPN Type, Parent Interface, Inner Tunnel IP Address/Mask, Endpoint and IPSec Profile
Step 4: Add IPsec Authentication like Type, Secret, Local ID Type. Click Done and then click Create Standard VPN.
8. Configure the Prisma Path Policy
9. Conclusion
Continue Reading...
- DNS Security over Cisco SDWAN : Cisco SDWAN Integration with Cisco Umbrella
- DNS Security & Proxy: Cisco Umbrella but Why? - The Network DNA
- Compare Zscaler Web Security and Cisco Umbrella: Which is Best?
- Cisco Security : Open DNS ( Cisco Umbrella ) - The Network DNA
- Palo Alto Prisma SDWAN 5.6 Release with 5G & CloudBlades
- Palo Alto Prisma SDWAN 5.5 Release with AlOps
- Introduction to Palo Alto's Prisma (CloudGenix) SDWAN








