Scenario : Dynamic NAT with PBR to multiple ISP Failover
In this scenario, we are going to discuss on the edge router which is connected to multiple Internet service providers use dynamic NAT with multiple outside interfaces and then ISP failover with Policy Based routing (PBR).
What is Network Address Translation (NAT) ?
By allowing several devices on a local network to share a single public IP address, Network Address Translation (NAT) is primarily used to save public IP addresses. When talking with external networks, it transforms private IP addresses used within a local network into a single public IP address.
Network Address Translation (NAT) operates at the OSI model's network layer (Layer 3). It changes the source and destination IP addresses in packet headers as they travel between the local and public networks.
- Static NAT: Maps a private IP address to a specific public IP address.
- Dynamic NAT: Maps private IP addresses to public IP addresses dynamically from a pool.
- NAT Overload (PAT): Maps multiple private IP addresses to a single public IP address using different port numbers.
What is Policy Based Routing (PBR) ?
With Policy Based Routing (PBR), you can set up routing based on criteria other than the destination network; PBR allows you to route traffic based on source address, source port, destination address, destination port, protocol, or a combination of these.
The primary purpose of Policy-Based Routing (PBR) is to provide network administrators with greater flexibility and control over how data packets are routed within a network. This goes beyond the limitations of traditional routing protocols which rely on destination IP addresses.
⭐Related : Understanding Policy Based Routing (PBR)
Scenario using Dynamic NAT & PBR
Below is the scenario where you can see we have 3 internet service provider for accessing internet name as ISP-1, ISP-2 and ISP-3.
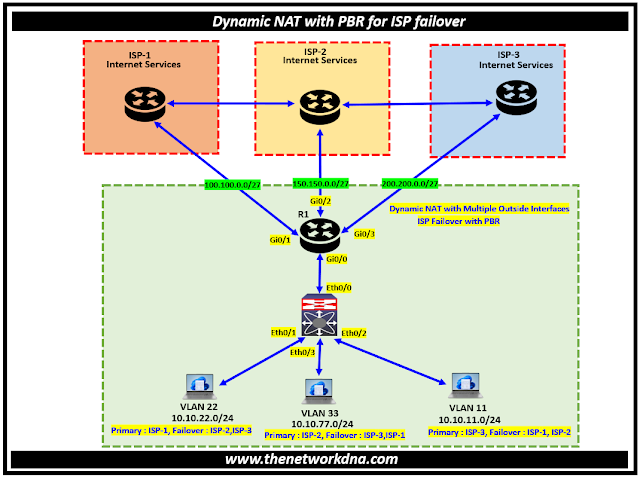 |
| Fig 1.1- Dynamic NAT with PBR to multiple ISP Failover |
We created three different NAT Pools for ISP-1, ISP-2 and ISP-3. we put the internet failover as below:
- VLAN 22 : Primary ISP-1, Failover to ISP-2 and ISP-3 respectively
- VLAN 77 : Primary ISP-2, Failover to ISP-3 and ISP-1 respectively
- VLAN 11 : Primary ISP-3, Failover to ISP-1 and ISP-2 respectively
NAT Pools
- ISP-1 : 100.100.0.3 - 100.100.0.10
- ISP-2 : 150.150.0.3 - 150.150.0.10
- ISP-3 : 200.200.0.3 - 200.200.0.10
Let's see the configuration on the Router R1 below for this setup
NAT Configurations on Router R1 as below
ip access-list extended ACL-NAT
permit ip 10.10.22.0 0.0.0.255 any
permit ip 10.10.77.0 0.0.0.255 any
permit ip 10.10.11.0 0.0.0.255 any
deny ip any any
!
ip nat pool ISP-1 100.100.0.3 100.100.0.10 netmask 255.255.255.224
ip nat pool ISP-2 150.150.0.3 150.150.0.10 netmask 255.255.255.224
ip nat pool ISP-3 200.200.0.3 200.200.0.10 netmask 255.255.255.224
!
route-map ISP-1 permit 10
match ip address ACL-NAT
match interface GigabitEthernet0/1
!
route-map ISP-2 permit 20
match ip address ACL-NAT
match interface GigabitEthernet0/2
!
route-map ISP-3 permit 30
match ip address ACL-NAT
match interface GigabitEthernet0/3
3
!
ip nat inside source route-map ISP-1 pool ISP-1
ip nat inside source route-map ISP-2 pool ISP-2
ip nat inside source route-map ISP-3 pool ISP-3
!
interface GigabitEthernet0/1
ip nat outside
!
interface GigabitEthernet0/2
ip nat outside
!
interface GigabitEthernet0/3
ip nat outside
!
interface GigabitEthernet0/0.1
ip nat inside
!
Now check, PBR Configurations on Router R1 as below
on the router as shown below
ip sla 100
icmp-echo 100.100.0.1 source-ip 100.100.0.2
threshold 200
timeout 250
4
frequency 3
!
ip sla schedule 100 life forever start-time now
!
ip sla 200
icmp-echo 150.150.0.1 source-ip 150.150.0.2
threshold 200
timeout 250
frequency 3
!
ip sla schedule 200 life forever start-time now
!
ip sla 300
icmp-echo 200.200.0.1 source-ip 200.200.0.2
threshold 200
timeout 250
frequency 3
!
ip sla schedule 300 life forever start-time now
!
track 100 ip sla 100 reachability
delay down 1 up 1
!
5
track 200 ip sla 200 reachability
delay down 1 up 1
!
track 300 ip sla 300 reachability
delay down 1 up 1
!
ip access-list extended ACL-VLAN22
permit ip 10.10.22.0 0.0.0.255 any
deny ip any any
!
ip access-list extended ACL-VLAN33
permit ip 10.10.77.0 0.0.0.255 any
deny ip any any
!
ip access-list extended ACL-VLAN11
permit ip 10.10.11.0 0.0.0.255 any
deny ip any any
!
route-map ACL-PBR-ISP permit 10
match ip address ACL-VLAN22
set ip next-hop verify-availability 100.100.0.1 10 track 100
set ip next-hop verify-availability 150.150.0.1 20 track 200
set ip next-hop verify-availability 200.200.0.1 30 track 300
6
!
route-map ISP-PBR permit 20
match ip address ACL-VLAN33
set ip next-hop verify-availability 150.150.0.1 10 track 200
set ip next-hop verify-availability 200.200.0.1 20 track 300
set ip next-hop verify-availability 100.100.0.1 30 track 100
!
route-map ISP-PBR permit 30
match ip address ACL-VLAN11
set ip next-hop verify-availability 200.200.0.1 10 track 300
set ip next-hop verify-availability 100.100.0.1 20 track 100
set ip next-hop verify-availability 150.150.0.1 30 track 200
!
interface GigabitEthernet0/4.1
ip policy route-map ACL-PBR-ISP
!
Hope this will clear the scenario with the configurations for NAT and failover to different ISPs based on the VLANs. You can switch the failovers as per your preferred ISPs accordingly. This configuration will give you an idea for traffic flows in this scenario.








