IPsec site-to-site VPN tunnel between two Palo Alto Firewalls
IPsec site-to-site VPN tunnel between two Palo Alto Firewalls
We are going to talk about the IPsec VPN tunnel between two Palo Alto Firewalls over the internet. we are configuring the tunnel between each site, avoiding overlapping subnets, so that a secure tunnel may be formed with the required security profiles applied.
⭐Related : Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls
⭐Related : IPsec site-to-site VPN tunnel between Palo Alto Firewall & FortiGate Firewall
Fig 1.1- IPsec site-to-site VPN tunnel
Start with the VPN connections, for that we must build zones.
Step 1: To create Zones, Navigate to Network > Zones
Provide the details like Name, Log Setting, Type and save.
Step 2: For Palo Alto devices (PA1 and PA2) with two LAN layers, we will generate the Address Object. To create Object, Navigate Object> Addresses
Provide the details like Name, Type and save
Step 3: Now as you created the object, we need to create the interface tunnel. To create Navigate to Network> Interface> Tunnel.
Provide the details like interface Name, Virtual Router, Security Zone and save.
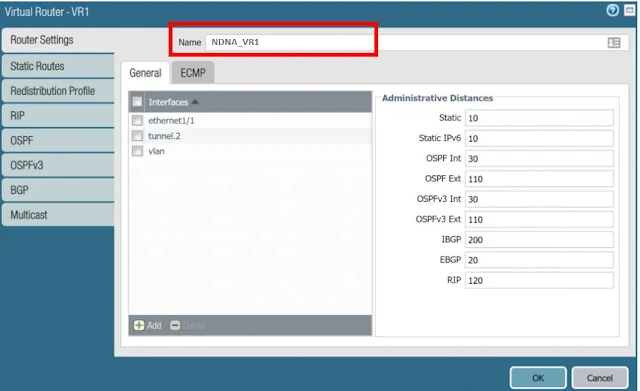
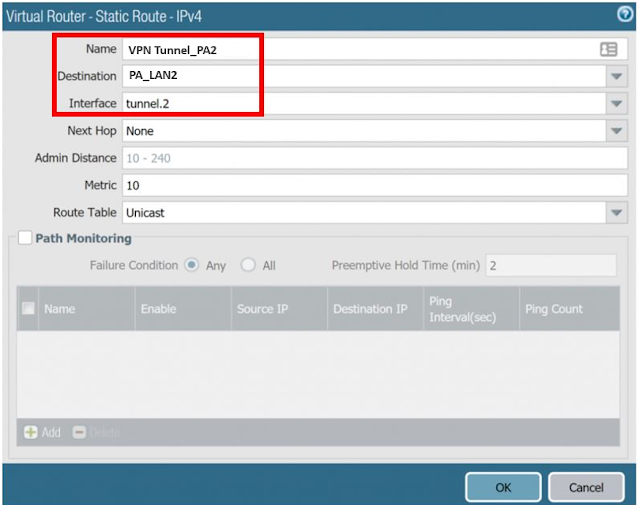
Step 4: Now create virtual routers .To create Navigate to Network > Virtual Routers> click ADD. Now Add Static Routes > IPv4
Step 5: Create IKE Crypto Phrase 1 for the VPN connection.
Navigate to Network--> Network Profile ---> IKE Crypto and Click on Add. (Phase 1)
Step 6: Similarly, create IPsec Crypto (Phase 2)
Navigate to Network > IPSec Crypto and click Add.
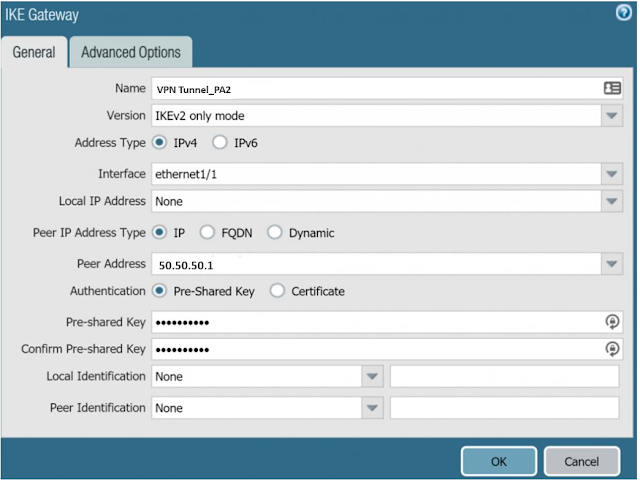
Step 7: Create IKE Gateways
Navigate to Network> IKE Gateways and click Add.
Name: VPN Tunnel_PA2
Version: IKEv2
Interface: ethernet1/1 (IPSec interface)
Peer IP Address Type: IP
Peer Address: 50.50.50.1
Authentication: Pre-Shared Key
Pre-shared Key: XXXXXX
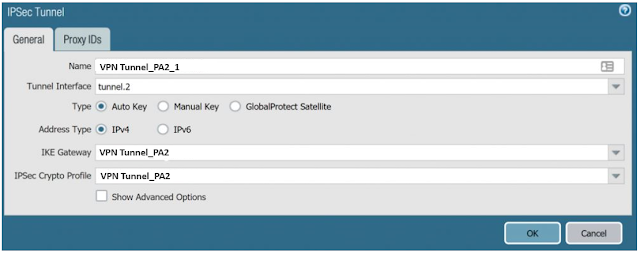
Step 8: Create IPsec Tunnels
Navigate to Network> IPSec Tunnels and press Add.
You can also add the proxy ID with the Local and Remote Network address
Step 9: Create Policy. Navigate to Policies > Security and click Add.
Configure the multiple tabs here like General, Source, Destination and Action
Similarly, we need to configure all the steps on PaloAlto PAN 2 device with the peer address of 25.25.25.1 and rest of the things as per your design.
⭐Related : Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls
⭐Related : IPsec site-to-site VPN tunnel between Palo Alto Firewall & FortiGate Firewall
Continue Reading...
- IPsec site-to-site VPN tunnel between Cisco ASA & FortiGate Firewall
- Site to Site IPSec VPN Tunnel between Cisco ASA and Palo Alto Firewalls
- Site-to-Site IPsec VPN Tunnel with two FortiGate Firewalls
- IPsec site-to-site VPN tunnel between Palo Alto Firewall & FortiGate Firewall
- Lan-to-Lan IPSEC VPN between two Cisco Routers
- Security: FortiGate to SonicWall VPN Tunnel setup
- How to configure IPSEC Tunnel configurations between two routers across Internet