Origin Validation for BGP in Juniper Networks
Origin Validation for BGP in Juniper Networks
If an administrator of an autonomous system (AS) starts advertising all or part of another company's allocated network, BGP has no built-in ability to detect the issue and respond in a way that avoids service disruptions.
Origin validation mitigates the vulnerability of transitive trust by allowing a provider to limit the advertisements it accepts from a client. The mechanics require the exchange of routing policies using an expanded BGP community attribute.
Routes are occasionally advertised inadvertently owing to operator error. To address this security vulnerability, set BGP to check the originating AS and reject invalid announcements. This functionality employs a cache server to authenticate prefixes or prefix ranges.
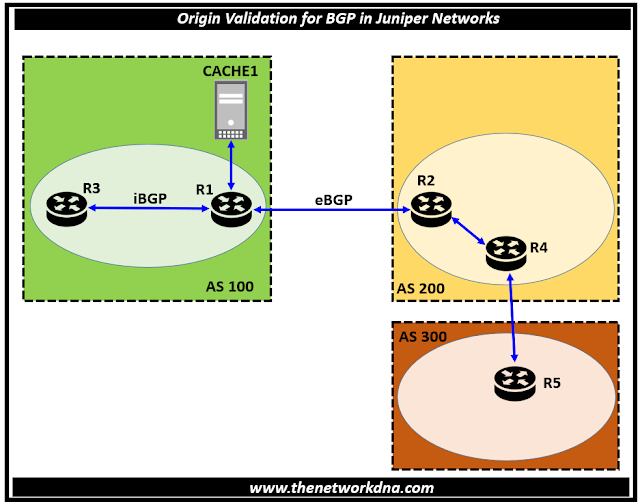
Fig 1.1- Origin Validation for BGP in Juniper Networks
In our scenario, Device R1 has an IBGP connection to Device R3 and an EBGP connection to Device R2. Device R1 gets route validation (RV) records from the cache server via the protocol defined in Internet document draft-ietf-sidr-rpki-rtr-19, The RPKI/Router Protocol.
The RPKI-Router Protocol communicates via TCP. Device R1 uses the RV records to create a local RV database. On Device R3, the validation status is configured using the BGP community called validation-state, which is received with the route.
⭐Related : BGP Cheat Sheet for Network Engineers
⭐Related : 51 facts about BGP routing Protocol for Network Engineers
Lets check the scenario and the configuration of the Router R1 here.
Router R1 Configurations
Configure the routing policy that specifies attributes to be modified based on the validation state of each BGP route.
user@R1# set autonomous-system 100
Hope it clarifies, we will come up with more details in a complex network in our next article related to Route origin validation (ROV).
Continue Reading...
- Why BGP-SRx is a Must-Have for Large Enterprises
- 51 facts about BGP routing Protocol for Network Engineers
- BGP Conditional Advertisement Feature
- Quick facts on BGP for interviews
- BGP Protocol : iBGP vs MP-iBGP protocol
- BGP : bgp deterministic-med and bgp always-compare-med
- BGP Attribute : AIGP-BGP Accumulative IGP