A Step-by-Step Guide to VXLAN Encapsulation Process
A Step-by-Step Guide to VXLAN Encapsulation Process
Virtual Extensible LAN (VXLAN) is a network overlay technology that enables the creation of virtualized Layer 2 (L2) networks over a Layer 3 (L3) network infrastructure.
VXLAN addresses the limitations of traditional VLAN-based L2 networks and provides several benefits that make it a popular choice for data center and cloud network virtualization.
Traditional VLAN-based networks are limited to 4,096 VLANs, which can be a major limitation in large-scale environments with many tenants or applications. With VXLAN, you can create up to 16 million logical networks, offering immense scalability potential. This makes it perfect for networks that need to expand quickly and reliably.
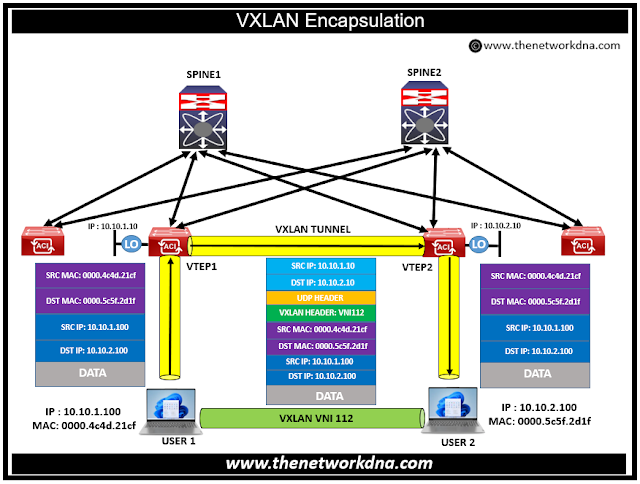
How VXLAN encapsulates and de-encapsulates an Ethernet frame ?
Lets take an example of two users (User 1 and User 2). User 1 and User 2 are standard hosts and do not have direct knowledge of VXLAN technology. VTEP1 and VTEP2 function as VTEP (VXLAN Tunnel Endpoint) switches in this setup. We utilize Virtual Network Identifier (VNI) 112 for encapsulating Ethernet frames exchanged between User 1 and User2.
Steps involved from USER 1 to VTEP 1
Step 1: User 1 sends out an Ethernet frame, which is intended for User2.
Step 2: Upon receiving this Ethernet frame at its VNI interface, VTEP1 executes several tasks:
Step 3: It identifies the VNI (in this case, 112) associated with User2.
Step 4: It then determines the correlation between the destination MAC address and the remote VTEP's IP address.
Step 5: VTEP1 proceeds to append a VXLAN header, tagged with VNI 112.
Step 6: Next, it includes a UDP header.
Step 7: It then adds an external IP header, configuring it with the IP addresses of VTEP1 and VTEP2.
Step 8: Finally, VTEP1 sends this IP packet over the underlying network.
Steps involved from VTEP 1 to VTEP 2 to USER2
Step 1: VTEP2, upon receiving the IP packet at its VTEP interface, performs its set of actions:
Step 2: It first removes the encapsulation from the IP packet.
Step 3: It verifies the correctness of the VNI and checks for any host associated with the destination MAC address.
Step 4: It then forwards the original Ethernet frame in the direction of User2.
- Arista Network datacenter design: Implementing VXLAN Routing
- Starting with VXLAN gateways - The Network DNA
- VTEPs and VNIs in VXLAN - The Network DNA
- Datacenter: VXLAN vs OTV - The Network DNA
- VLAN vs VXLAN : Towards Next Generation Networks
- VXLAN vs QinQ - The Network DNA
- NGN virtualization encapsulation: GENEVE vs VXLAN
- Datacenter: Troubleshooting steps for EVPN VXLAN DC environment
- VXLAN Encapsulation and Packet Format
- Cisco Datacenter: Inter-VXLAN Routing Design
- VXLAN BGP EVPN : VXLAN Control Plane
- Juniper VXLAN Configs: Configuring VXLANs on Juniper MX Series Routers
- Overview on VXLAN in the Fabric Network- Cisco ACI