Network Based Firewall Vs Host Based Firewall
Network Based Firewall Vs Host Based Firewall
As technology advances at an unprecedented pace, robust cybersecurity protects are more essential than ever. With cyber risks hiding around every corner of the digital world, organizations and individuals must take proactive measures to safeguard their sensitive information. Network-based firewalls and host-based firewalls are two of the most popular and debatable cybersecurity tools.
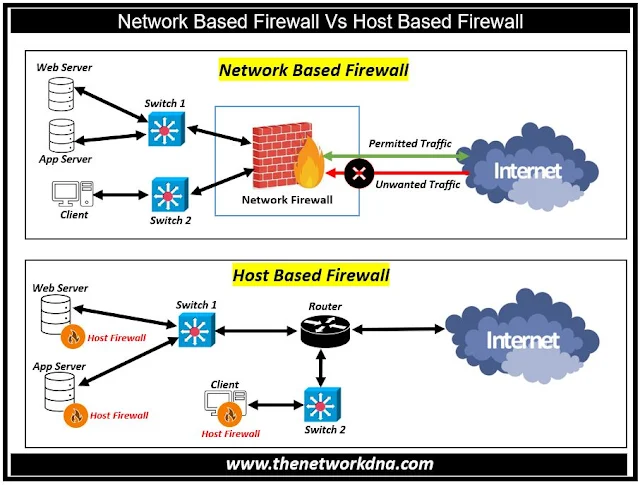 |
| Fig 1.1- Network Based Firewall Vs Host Based Firewall |
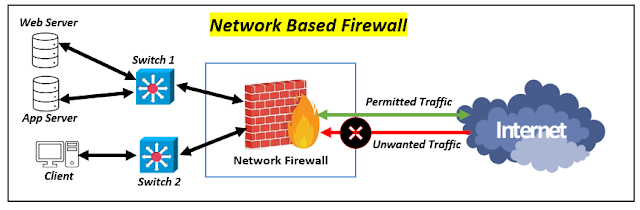
⭐ Understanding Network Based Firewall 👇
Network-based firewalls are probably the most popular and widely used kind of firewall protection. These firewalls, as the name implies, are implemented at the network level, typically within an organization's router or gateway, where they can monitor and restrict the flow of traffic in and out. Network-based firewalls can enforce established security rules by analyzing incoming and outgoing packets to prevent unwanted or potentially destructive traffic from reaching a network.
A network-based firewall's ability to provide a centralized point of security for a complete network is one of its primary benefits. By protecting a network's entry and exit points, these firewalls can effectively filter out threats before they reach individual devices or systems. This centralized solution also simplifies network traffic management and monitoring because all traffic can be evaluated and handled from a single location.
It is crucial to note, however, that network-based firewalls have limits. While they may be effective in filtering inbound and outbound traffic, they may fall short of detecting and preventing attacks that originate within the network. Furthermore, network-based firewalls are ineffective in protecting individual devices connecting to the network from remote places, such as remote employees or third-party contractors.
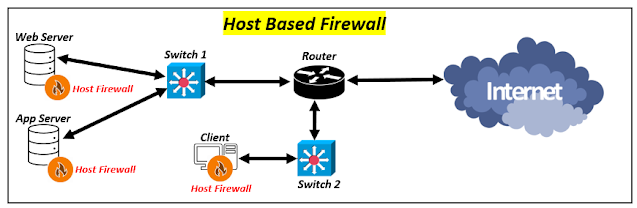
⭐ Understanding Host Based Firewall 👇
Host-based firewalls, in contrast to network-based firewalls, perform at the device level. These firewalls can be set up locally on a device, such as a machine or server, and have the ability to monitor and control traffic particular to that device. Host-based firewalls are especially useful for preventing devices that may be exposed to attacks while linked to remote networks, such as free wireless hotspots or unauthorized internet access points.
One of the primary benefits of host-based firewalls is their ability to give granular control over traffic entering and exiting a single device. Host-based firewalls can prevent unauthorized access and guard against malicious software that attempts to exploit vulnerabilities at the device level by creating unique rules and permissions for each device. Furthermore, host-based firewalls can monitor and stop suspicious behaviors that a network-based firewall may not notice.
Host-based firewalls, regardless of their efficiency in protecting individual devices, have limits. For example, maintaining and managing host-based firewalls throughout an enterprise can be a difficult and time-consuming operation
⭐ Network Based Firewall Vs. Host Based Firewall 👇
When comes to the comparison between Network based and the host based firewall, you cam look the below table to understand more
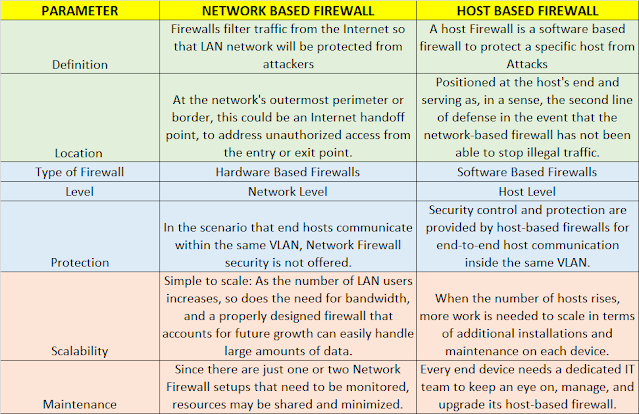 |
| Fig 1.2- Network Based Firewall Vs Host Based Firewall |
In actuality, a lot of businesses could discover that the best way to secure their digital assets is to use a mix of host-based and network-based firewalls. Organizations can build a multi-layered defensive plan that guards against a variety of threats from both within and outside the network by utilizing the advantages of both types of firewalls.
Organizations may benefit from the best of both worlds with this hybrid solution, which can safeguard individual devices precisely and controllably while also offering robust network security.
The optimal strategy for a company ultimately depends on its particular security needs, business operations, and data handling requirements. Both types of firewalls have advantages and disadvantages. Organizations can make well-informed decisions that are in line with their security aims and goals by carefully weighing the advantages and disadvantages of each type of firewall.
- Security Dose 06122023- Nonrepudiation and its implementation!
- Security Dose 28112023: Primary Goals & Objectives of Security Infrastructure
- Security Dose 231123 - It's about Security!!
- Security: Cisco ASA Vs Cisco FTD
- Site-to-Site VPN: IPSEC Tunnel Between an ASA and a Cisco IOS Router
- Cisco Security: Cisco ASA 5505 Interfaces configuration for Access Ports
- Cisco ASA Series 1: Restoring the ASA to Factory Default Configuration