Introduction to Azure Network Security Group (NSG)
Introduction to Azure Network Security Group (NSG)
An Azure Network Security Group (NSG) is a firewall or access control list that manages network traffic to and from Azure resources inside a virtual network. It gives you the ability to construct rules that filter traffic based on IP address, port, and protocol.
The rules may be applied to individual virtual machines or subnets to manage access to resources like as virtual machines, load balancers, and application gateways.
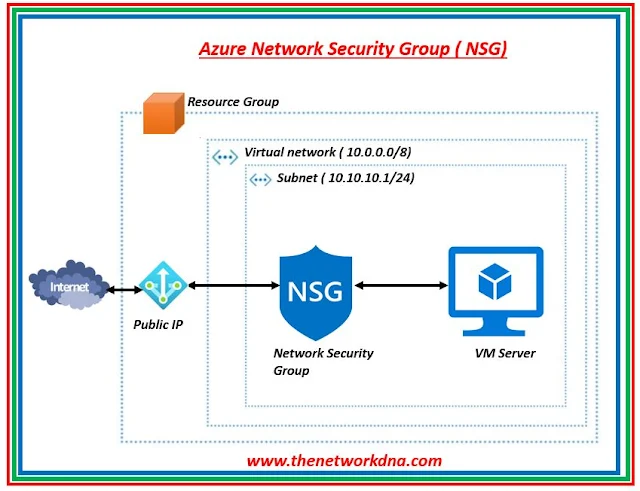 |
| Fig 1.1- Azure Network Security Group (NSG) |
Azure NSGs can aid in the protection of your resources against unauthorized access and other harmful actions. NSGs can be linked to subnets or specific virtual machine instances inside those subnets.
On the Azure portal, you will see below to configure your Network security group ( NSG)
 |
| Fig 1.2- Azure Network Security Group (NSG) |
- Control over inbound and outbound network traffic: You may manage access to resources like virtual machines, load balancers, and application gateways by using NSGs to build rules that filter traffic based on IP address, port, and protocol.
- Protection against unauthorized access: By blocking undesirable traffic, NSGs can assist in defending your resources against unauthorized access and other harmful actions.
- Granular security: You may define granular security policies with NSGs that can be applied to specific virtual machines or subnets.
- Scalability: NSGs may be utilized across numerous virtual networks and are simply scalable to adapt to changes in your network environment.
- Automation and Integration: For centralized administration and cutting-edge security capabilities, NSGs may be automated and linked with other Azure services like Azure Security Center, Azure Policy, Azure Monitor, and Azure Automation.
Every network security group has a set of default rules. The default rules cannot be deleted, but because they have the lowest priority, they can be replaced by the rules you make.
Network security group and virtual machine affiliation
When you link a network security group to a virtual machine, all incoming and outgoing traffic is subject to its network access policies.
NIC and network security group affiliation
The network access restrictions of a network security group only apply to the NIC with which it has been associated. As a result, traffic connected to other NICs in a virtual machine with multiple NICs is unaffected when a network security group is applied to a single NIC.
Connecting a subnet to a network security group
All of the IaaS and PaaS resources in the subnet are subject to the network access rules of the network security group when a subnet is associated with it.
Depending on the deployment type, you may assign several network security groups to a virtual machine (or NIC) as well as the subnet that a NIC or virtual machine is connected to. When this occurs, each network security group's priority-ordered set of network access rules is applied to all traffic.
Inbound traffic
- The packet will be deleted if a network security group on the subnet has a matching rule to deny traffic.
- Even if the network security group on the subnet has a match rule to allow traffic, if the network security group of the virtual machine or the NIC has a matching rule to reject traffic, the packet will be discarded in the virtual machine or the NIC.
Outbound traffic
- The packet will be deleted if the virtual machine's network security group or the NIC has a matching rule to refuse traffic.
- Even if the network security group on the virtual machine or the NIC has a matching rule to allow traffic, if the network security group on the subnet has a matching rule to reject traffic, the packet will be deleted at this point.
++++++++++++++++++++++++++++++++++++++++++++++++++++
Introduction to Azure Express Route - The Network DNA
Learn about Azure UDR (User Defined Routes) - The Network DNA
Gateway Types in Azure - The Network DNA
Introduction to Azure Virtual Network (VNET) - The Network DNA
++++++++++++++++++++++++++++++++++++++++++++++++++++







