Exploring the Key Differences: RADIUS vs TACACS+
Exploring the Key Differences: RADIUS vs TACACS+
TACACS+ and RADIUS are two protocols used in the AAA (Authentication, Authorization, and Accounting) system to enable centralized authentication for network users. Lets talk about both one by one in simple words.RADIUS (Remote Authentication Dial-In User Service)
RADIUS (Remote Authentication Dial-In User Service) is a server system that protects our networks against unauthorized access. As a result, RADIUS clients execute on routers and switches that are supported. Clients transmit authentication requests to a centralized RADIUS server, which stores all user authentication and network service access data.
To put it another way, RADIUS is a network protocol that defines rules and norms for communication between network devices - specifically, for remote user authentication and accounting. Uses UDP port 1812 for authentication and 1813 for accounting. Legacy ports are 1645 and 1646.
⭐Read: Introduction to RADIUS- Remote Authentication Dial-In User Service
 |
| Fig 1.1- RADIUS Server Authentication |
What is the primary function of RADIUS servers?
The primary function of the RADIUS server in the network is detailed below.
- Authenticates people or devices before granting them network access.
- Allows particular people or devices to utilize specific network services.
- Accounts for and monitors the utilization of those services
TACACS+ (Terminal Access Controller Access Control System)
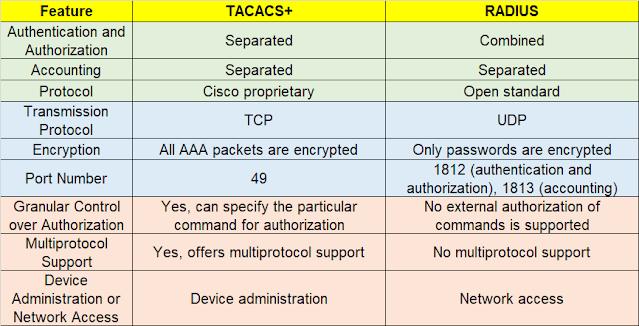 |
| Fig 1.2- RADIUS Vs TACACS+ |
Continue Reading...
- Verify TACACS between Cisco ISE and Cisco DNA center
- AAA Authentication Process: AAA Authentication login
- How to Configure RADIUS Authentication on Cisco Viptela vEdge/cEdge devices
- Cisco Meraki: Add ISE as a RADIUS Server for Dot1x SSID
- Add ISE as a RADIUS Server for Wired 802.1X
- Cisco Meraki : Add ISE as a RADIUS Server for Guest SSID







