Security Dose: Snooping Attack
Security Dose: Snooping Attack
In this article, we are going to talk about common security
threats. As you know modern enterprise networks are no longer limited to
branches and data centers. Today networks extend to everywhere for users to
connect and access applications hosted in the cloud. When we talk about this
network trend where perimeter does not exist, security becomes a major concern
for organizations. It is very difficult to secure a network that is out of your
administrative control.
Understanding different types of security threats and
understanding the mitigation helps organizations maintain the confidentiality,
integrity, and availability of the applications or other critical assets.
Spoof Attacks
In a normal scenario, the communication between two
endpoints is simple where each packet going to have a source address and the
destination address to identify the sender and the receiver of the information
on the network. This is true for any kind of communication over the network.
Several attacks replace the original sender or destination
information on the packet and try to overload the network by sending a packet
from the source to a destination that does not exist on the network. These
attacks are called spoof attacks. For instance, let’s say an attacker snoop an
IP packet and replaces the Source Packet with another IP address that does not
exist on the network. Once the request comes to a server, the server sends the
response to the forged IP address that does not exist and then dropped
eventually in the network.
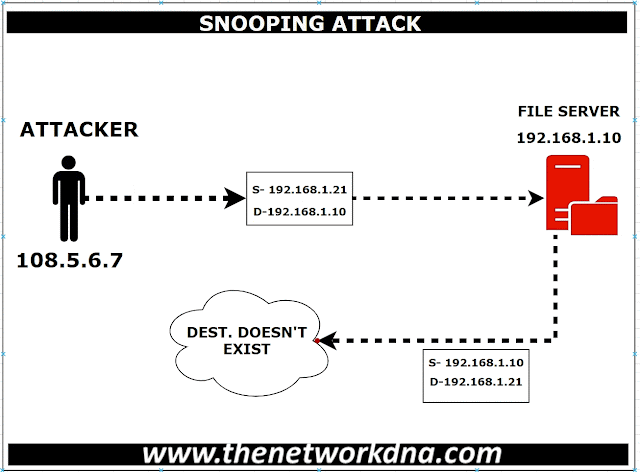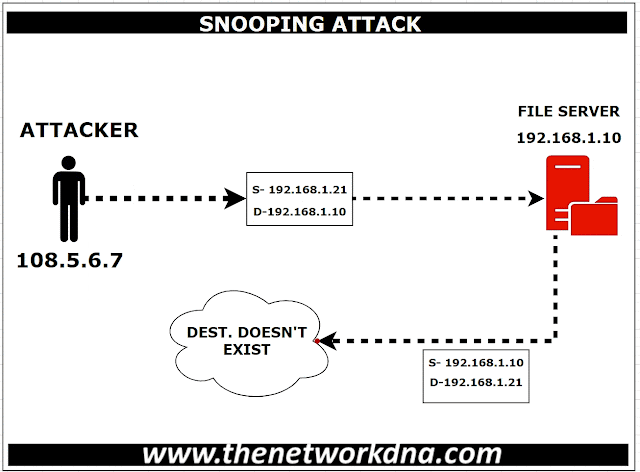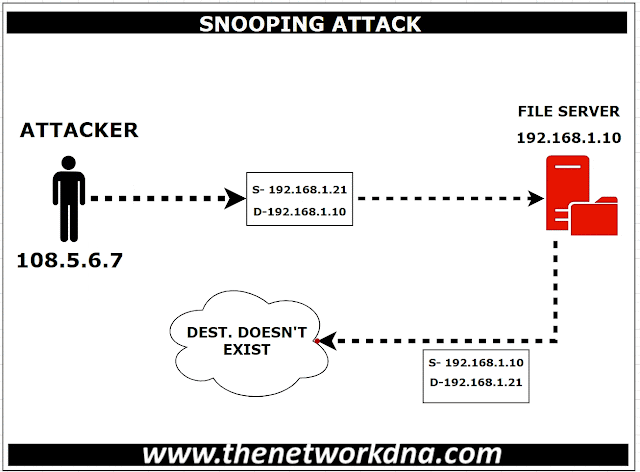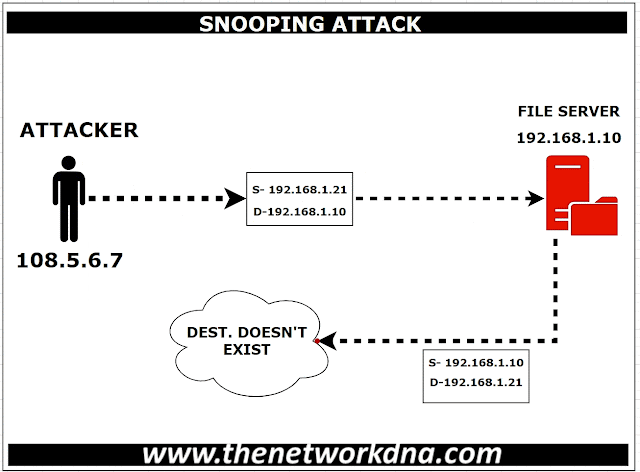 |
| Figure 1: Address spoofing attack! |
Address spoofing applies to the layer 2 MAC address too. An
attacker can spoof the MAC address and create a DHCP request for an IP address
assignment. DHCP after receiving this request, reserves the IP address that
will not be used in the network. This way attacker can impact the DHCP function
where there is no IP left for new hosts on the network.
Features like port security, DHCP snooping, and ARP
inspection can be used to prevent snooping attacks on the network. Hope you
find this informative!







