OSI Model : Application Layer Services and Protocols-II
OSI Model : Application Layer Services and Protocols-II
A single application may use a variety of Application layer services, thus what appears to the user as a single request for a web page may actually be hundreds of distinct requests. Additionally, many processes may be performed for each request. A client, for example, may require numerous distinct processes to create a single request to a server.
Furthermore, servers frequently have numerous clients seeking information at the same time. A Telnet server, for example, may have several clients seeking connections to it. For the network to function properly, these individual client requests must be processed concurrently and individually. To properly handle the many interactions, the application layer processes and services rely on help from lower layer activities.
⚡ Peer-to-Peer Networking and Applications (p2p) 📜
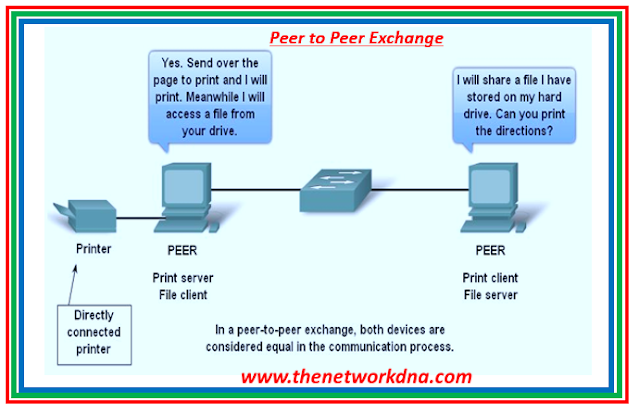
Peer-to-peer networking may be divided into two categories: peer-to-peer network architecture and peer-to-peer applications (P2P). Both kinds have comparable characteristics but function considerably differently in practice.Fig 1.1- Peer to Peer
A peer-to-peer network connects two or more computers via a network and allows them to share resources (such as printers and files) without the need for a dedicated server. Every connected end device (referred to as a peer) can act as a server or a client. One machine may operate as a server for one transaction while also acting as a client for another. The client and server roles are assigned each request.
A peer-to-peer network is illustrated with a modest home network with two linked PCs sharing a printer. Each computer may be configured to exchange data, play networked games, or share an Internet connection. Another example of peer-to-peer network capability is two computers connecting to a big network and sharing resources via software applications via the network.
Peer-to-peer networks, as opposed to the client/server paradigm, decentralize network resources. Instead of locating information to be shared on dedicated servers, information may be located anywhere on every connected device. Most modern operating systems offer file and print sharing without the need for extra server software. Because peer-to-peer networks do not often employ centralized user accounts, permissions, or monitors, it is difficult to implement security and access regulations in networks with more than a few machines. User accounts and access privileges must be configured separately on each peer device.
⚡ Peer-to-Peer Applications 📜
In contrast to a peer-to-peer network, a peer-to-peer application (P2P) allows a device to function as both a client and a server inside the same transaction. In this architecture, every client is a server, and every server is a client. Both can begin communication and are treated equally in the communication process. Peer-to-peer applications, on the other hand, necessitate that each end device offer a user interface and execute a background service. When you run a certain peer-to-peer apps, it activates the necessary user interface and background services. After that, the gadgets can communicate directly.
Some P2P applications use a hybrid system where resource sharing is decentralized but the indexes that point to resource locations are stored in a centralized directory. In a hybrid system, each peer accesses an index server to get the location of a resource stored on another peer. The index server can also help connect two peers, but once connected, the communication takes place between the two peers without additional communication to the index server.
Peer-to-peer applications can be used on peer-to-peer networks, client/server networks, and across the Internet.
Continue Reading...
- Introduction to the NAT, PAT, Dynamic NAT and Static NAT
- Cisco Viptela SDWAN: NAT Mapping and Filtering Test
- Decoding SNAT and DNAT: Unveiling the Variances
- A brief about PAT- Port Address Translation
- NAT Overloading akka PAT inside global addresses
- Forward Proxy Vs Reverse proxy
- Concept of Reverse proxy
Free Tools...