Step-by-Step: How to Perform Packet Capture on Cisco Switches
Step-by-Step: How to Perform Packet Capture on Cisco Switches
💥💥 BLACK FRIDAY DEALS AMAZON" 💥💥
62% off Echo Show 8 (2nd Gen)
51% off Beats Studio Pro
61% off Sunzel Flare Yoga Pants
$500 off Peloton Bike+
Packet capture and packet analysis are made possible by the multi-step packet capture protocol (PCAP), which makes use of many tools. Packet sniffers are tools used to do packet capture; they are the first step in the process. Hardware-based packet sniffers are also referred to as taps.
They are often computer software that run on a network-connected device, such as a PC. The packets intercepted by the packet sniffer are saved in a PCAP file, which is produced once it is connected. The file should include timestamps for each capture as well as information about the data that was recorded during the operation.
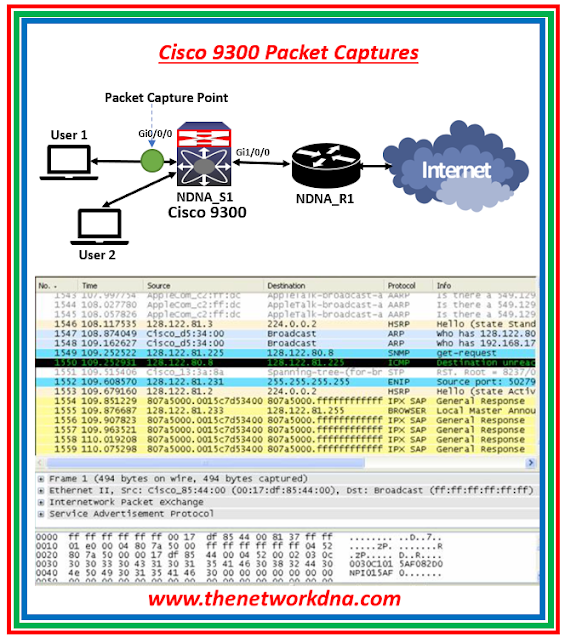 |
| Fig 1.1- Cisco Catalyst 9300 PCAP |
⚡Note: Wireshark is supported only on switches running DNA Advantage
⚡Note: Make sure there is enough memory (at least 200 MB) and that CPU use is modest before beginning a Wireshark capture procedure. The number of packets that fit the preset criteria and the planned actions (storage, decode and display, or both) for the matched packets determine how much CPU is used during Wireshark capture.
⭐Restrictions of Configuring Wireshark👇
- Wireshark does not allow global packet capture.
- It is not possible to restrict circular file storage by file size.
- DNA Advantage has a file limit that is determined by the flash's size.
- On a destination SPAN port, packets cannot be captured by Wireshark.
- When an interface or attachment point connected to a capture point ceases to function, Wireshark ceases to capture. As an illustration, suppose the attachment point-related equipment is disconnected from the device. One must manually restart the capture in order to continue.
- A Wireshark class map can have just one authorized ACL (IPv4, IPv6, or MAC).
⭐Cisco Catalyst 9K Packet Captures👇
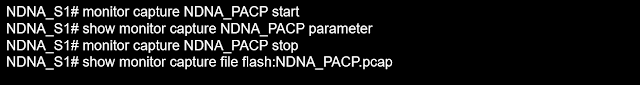
When the packet capture process begins, the sniffer captures data packets as they transit over the network and stores those copies for examination. The below captures commands are taken on Cisco Catalyst 9300 Switch as an example.
We must specify the sort of traffic we want to collect. Here is an example setup for collecting IPv4 traffic in both directions on a specified Port.
The captured packets will be stored to the Switch's buffer. It is typically better to export a capture to a standard format for detailed investigation PCAP file, You can check that in Wireshark.
Now that the PCAP file is safely saved on the Switch Flash, we may use Wireshark to open and export it. Always check that there is enough space on the Flash (although the file sizes shouldn't be too large for quick captures), and monitor the Switch's CPU while the capture is in progress.
Continue Reading...
- 51 facts about BGP routing Protocol for Network Engineers
- BGP Protocol : iBGP vs MP-iBGP protocol
- BGP : bgp deterministic-med and bgp always-compare-med
- Part 1: 5 BGP commands rarely used
- BGP: Path Selection Criteria - Path Vector Protocol
- BGP Attribute : AIGP-BGP Accumulative IGP
- Part 2: 5 BGP commands rarely used
- BGP Basics: BGP Neighbor States
- Part 3: 5 BGP commands rarely used
- 10 Interview questions on BGP Routing Protocol
- BGP Protocol: BFD C Bit Feature
- BGP Advance Feature Non Stop Forwarding- NSF