Understanding the Flaw: How the Cisco Catalyst SD-WAN Manager Can be Accessed Remotely
Understanding the Flaw: How the Cisco Catalyst SD-WAN Manager Can be Accessed Remotely
Cisco has issued a security advisory on five new Catalyst SD-WAN Manager product vulnerabilities, the most serious of which allows unauthenticated remote access to the server.
Cisco Catalyst SD-WAN Manager for WAN is network management software that allows administrators to visualize, install, and monitor WAN devices.
CVE-2023-20252 (CVSS v3.1: 9.8) is the most serious of the published holes affecting the product, allowing unauthorized access due to weaknesses with the Security Assertion Markup Language (SAML) APIs.
"A vulnerability in the Security Assertion Markup Language (SAML) APIs of Cisco Catalyst SD-WAN Manager could allow an unauthenticated, remote attacker to gain unauthorized access to the application as an arbitrary user," states the security warning.
The weakness may be exploited by sending specially designed queries straight to the SAML APIs, which produce arbitrary authorization tokens that grant the application unfettered access.
- CVE-2023-20252 exploits have the potential to cause user impersonation, unauthorized data access/modification/deletion, and service interruption.
- CVE-2023-20253 (CVSS v3.1: 8.4): Unauthorized configuration rollback due to CLI vulnerabilities.
- CVE-2023-20034 (CVSS v3.1: 7.5): Information disclosure vulnerability in Elasticsearch access control.
- CVE-2023-20254 (CVSS v3.1: 7.2): Authorization bypass in the session management system. (requires multi-tenant feature enabled)
- CVE-2023-20262 (CVSS v3.1: 5.3): DoS vulnerability in the SSH service. (affects SSH access only)
 |
| Fig 1.1- Cisco SDWAN Manager Vulnerability |
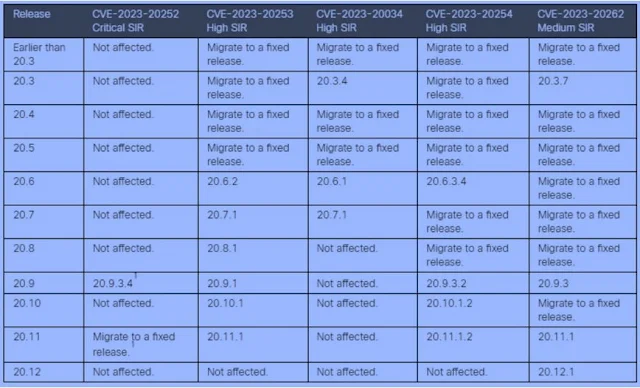
CVE-2023-20252, the most critical to repair, affects versions 20.9.3.2 and 20.11.1.2 but not prior releases in the 20.9 and 20.11 branches.
Except for the medium severity defect (fixed in 20.12.1), Catalyst SD-WAN Manager version 20.12 is unaffected by any weaknesses, making it the safest version to update to if feasible.
This time, Cisco has provided no solutions for the addressed issues, therefore the only advised action is to upgrade to a patched release.
IOS XE Software, SD-WAN cEdge Routers, and SD-WAN vEdge Routers are not susceptible, according to the vendor.
Although none of the weaknesses have been found to be actively exploited, updating to the recommended versions should be done as soon as possible.
More details on below note
Cisco Catalyst SD-WAN Manager Vulnerabilities








