DNS Tunneling and Prevention
DNS Tunneling and Prevention
Before we are going to start with the DNS Tunneling, lets talk about DNS first. The system that automatically converts internet addresses to the numeric machine addresses that computers use is known as a domain name server.
⭐What is DNS Tunneling 👇
DNS tunneling is a sort of cyber attack that uses the Domain Name System (DNS) protocol to tunnel malware and other data through a client-server paradigm.
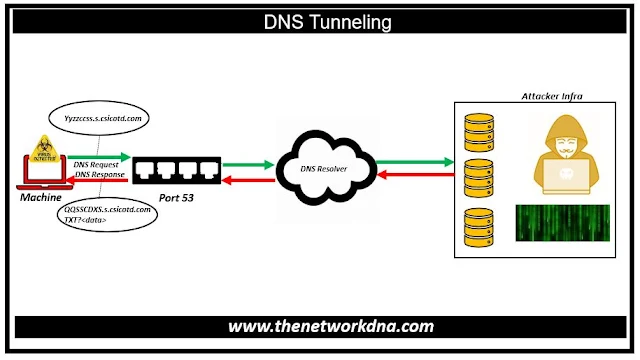
The attacker registers a domain name and directs its name server to their server, which contains a tunneling malware software. The attacker installs malware on a computer, which is frequently hidden behind a company's firewall.
The compromised computer queries the DNS resolver, which forwards IP address requests to root and top-level domain servers. The query is routed by the DNS resolver to the attacker's command-and-control server, where the tunneling program is installed. Through the DNS resolver, a connection is now formed between the victim and the attacker. This tunnel can be exploited for data exfiltration or other illegal purposes.
⭐Detection of DNS Attack 👇
- Monitoring DNS traffic for unusual patterns, such as a high frequency of requests, long domain names, or the presence of encoded data within DNS payloads.
- Excessive queries for one domain with many subdomains
- Excessive DNS queries from one source
- Excessive amount of odd query types : TXT, CNAME, MX, NULL LONG/random looking subdomains
- Encoded data in TXT responses
- Usage of unauthorized DNS servers
⭐How to Prevent DNS👇
DNS is an extremely robust mechanism that is used practically everywhere to look up resources and services with which to interact.
DNS offers a communication foundation that allows higher level and more sophisticated protocols to function, but it is often disregarded in terms of security, especially given how much malware is distributed via email protocols or downloaded from the web via HTTP.
Organizations can protect themselves from DNS tunneling in a variety of methods.
- Domain names (or IP addresses or geographical locations) are blocked depending on their reputation or perceived threat.
- Rules around “strange looking” DNS query strings.
- Rules around the length, type or size of both outbound and inbound DNS queries.
- General hardening of the client operating systems and understanding the name resolution capabilities as well as their specific search order.
- User and/or system behavior analytics that automatically spot anomalies, such as new domains being accessed especially when the method of access and frequency are abnormal.